Several cyber specialists warn about Mantis, the mantis, which would be the most powerful botnet known to date. It would target, in particular, Android and iOS users based in France.
Last month, content provider Cloudflare recorded the biggest DDoS attack in its history. Behind it, we find the Mantis botnet, capable of generating an attack of, hang on tight, 26 million requests per second. And all this using the trifle of 5,000 bots only. After hitting some of our neighbors or powers, he is now attacking French Android and iOS users, through phishing and malware attacks.
This mantis is not pretty: it is destructive
The Mantis botnet is closely studied by digital and cyber players such as Cloudflare or Sekoia. Nearly a thousand Cloudflare customers have, for example, been affected by this new network of bots, which could well be the worthy descendant of Meris. Thousands of machines have in any case been compromised. More than just a mantis, Mantis might even be compared more to the Mantis shrimp: small yet mighty.
If it only operates a fleet of 5,000 devices, Mantis can generate massive force, and become responsible for the most powerful DDOS attacks by HTTPS requests ever observed. ” It is observed that it is difficult to generate so many HTTP requests without additional cost, but Mantis did it by HTTPS “confirms Cloudflare.
HTTPS DDoS attacks require more computational resources, partly because of the higher cost of establishing a secure TLS encrypted connection. ” This highlights the unique force behind this botnet adds the American company.
French Android and iOS users not spared by Mantis
Unlike more traditional botnets, which transit via low-bandwidth connected objects, Mantis operates virtual machines and powerful servers. Each bot therefore has much greater computing resources. Without question, Mantis is the next evolution of the Meris botnet, which relied on MikroTik devices (which notably manufactures routers).
So what does Mantis do? Sekoia explains that the group behind the botnet deposits, on Android devices, the XLoader payload, known to be an Android spyware and banking Trojan developed by Yanbian Gang, a group of Chinese cybercriminals. XLoader can range from using DNS spoofing to distribute infected Android apps (to collect personal and financial information) to using SMS communication to trick users into downloading malware onto their Android device. Moreover, even the target using an iOS device can fall into the trap, being redirected to a phishing page to steal their Apple IDs.
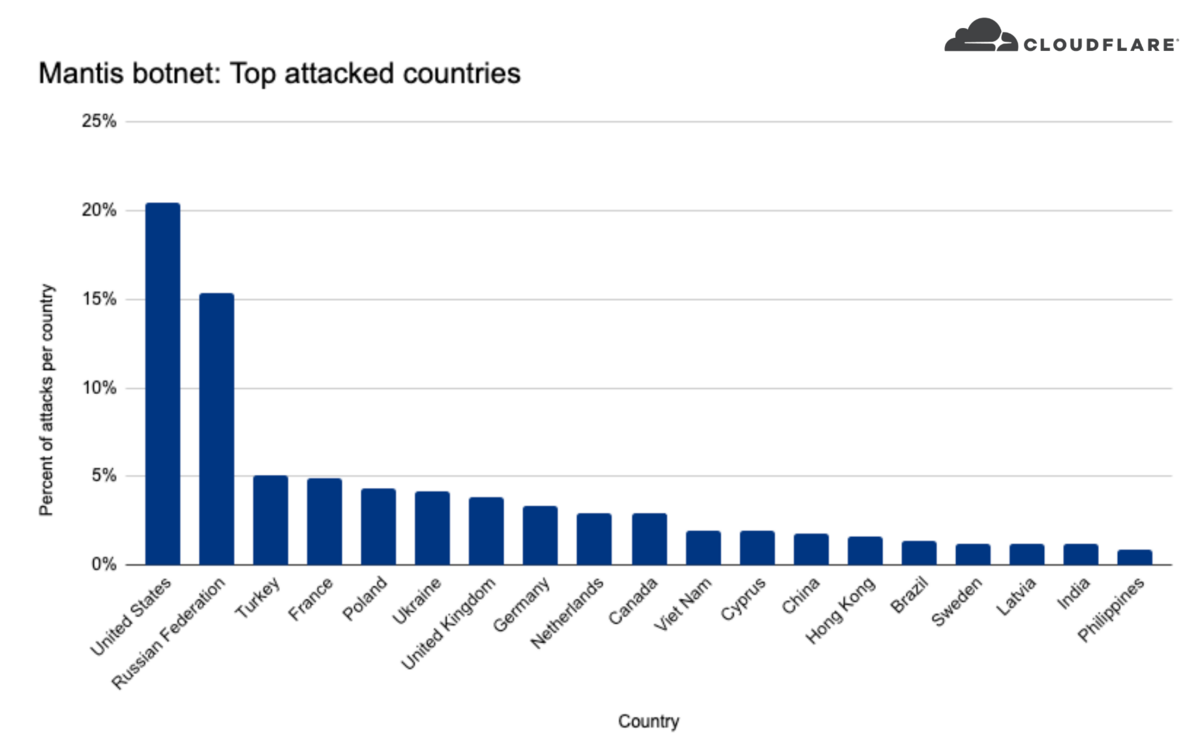
The global telecom and Internet sector is the most affected by Mantis, with 36% of attacks. The media, video game publishers and finance follow. As for the targets from a geographical point of view, 20% of DDoS attacks would concern companies based in the United States, 15% in Russia, and less than 5% in Turkey, Poland, Ukraine and France. Taiwan, the United Kingdom, South Korea and Japan are also affected.
In France, Mantis can manifest itself by an SMS sent, encouraging you to follow a URL. This may, for example, relate to a package that has supposedly been sent to you and which needs you to arrange its safe delivery. If the potential victim uses iOS, he is then redirected, as we said, to a phishing page that steals the identifiers. Android users are directed to a site that provides the installation file for a mobile application.
The APK then runs and mimics a Chrome installation that comes asking you for multiple permissions on your device (SMS, calls, reading and writing storage, etc.). Tens of thousands of people may already have been trapped, says Sekoia.
Source : Cloudflare, Sekoia

9