Libertarianism in the age of crypto
Crypto-anarchists, who advocate the use of cryptography via public and private keys in an effort to enhance secrecy, anonymity, and private privacy on the Internet, may be off to a bad start by using Bitcoin to achieve their privacy desires. To put it simply, these individuals see state control as a central surveillance body from which, among other things, all personal information transmitted on the Web would be spied on.
To fight against this centralized structure embodied by the State, one of the responses envisaged would be, according to them, the establishment of a decentralized public structure removed from control by concealment of identities and personal information that would make possible cryptography. On the other hand, it is naive, in my opinion, to believe that the Bitcoin code makes it possible to evade state control, the jurisdictions of a territory, censorship on the Internet, personal data retention or taxation. . A little technical reminder of what a public blockchain is seems relevant to me before continuing.
The transparency of the public blockchain
Bitcoin is based on a distributed database, in other words, it is presented as a network composed of several machines (called “nodes”) capable of calculating a gigantic number of mathematical operations in order to find the one-block solution to validate the user transactions. In this Bitcoin network, each transaction carried out is necessarily attached to a block which is itself attached to the previous block and all of whose information is public and transparent.
Succession of blocks on Bitcoin
investing
Technically speaking, this transparency is manifested by the fact that, to set up the software which makes it possible to mine bitcoins on a machine (the famous node) it is necessary to hold an integral copy of the Bitcoin blockchain since its launch in 2009. A copy that is downloadable without any conditions, except having Internet access. This means that the transactions are fully available and engraved in the blockchain, therefore open and accessible to all.
There is nothing opaque about these blocks of transactions. The amount of the transactions, their time as well as the identifier of the sender and the recipient (in alphanumeric format of the type = 9172e6rtc99f144f72eca9a569412580azopt2cfd174567f07e657569493bc44) are perfectly traceable on the chain. The purpose of cryptographic encryption on Bitcoin is therefore not so much to conceal the existence of transactions but rather to guarantee their authenticity, i.e. their non-falsification from malicious modification. But then, in concrete terms, how can this incomprehensible alphanumeric identifier be traced? American researchers from the University of Houston have looked into the matter.
Anonymity pales in Bitcoin
I spare you the exposure of all the mathematical-computer-economic-cryptographic methods used by American researchers to trace transactions on the Bitcoin network. But overall, the social aspect of users has been studied under the prism of Pareto’s law, Nash’s equilibrium, the Centipede game and the Centipede game. The cryptographic side was treated with the method of linear bindings of addresses, the tracing of extranonces, the analysis of metadata and the “follow-the-money” strategy. Find the full document of the researchers here: Cooperation between an anonymous group protected by Bitcoin during the failures of decentralization
The researchers explain that identity masking (represented by an alphanumeric public key) on Bitcoin can be compromised by the address binding mechanism, i.e. determining, using cryptographic tools, if an actor controls several addresses. In particular by analyzing the behavior of a sender and receiver address. Therefore, an anonymity-minded user should frequently generate new public/private key pairs and not reuse previous public keys.
In practice, the researchers point out that users frequently reuse the same key pairs and move bitcoins in an easily characterizable way that, in effect, leaks personal information or information regarding the nature of the transaction. Metadata from these transaction practices can be used to assign multiple public keys to the same entity or agent.
Furthermore, the fact that users occasionally perform transactions in a very idiosyncratic way, for example by repeatedly transferring very specific quantities of bitcoins, reveals mathematical patterns that make it possible to link the addresses involved by the same actor.
Note that, if bitcoin users wish, they can generate as many addresses as they wish using the bitcoin software (white nodes). These addresses, which function as pseudonyms for the user, allow them to mask their activity. But address-binding strategies undermine this pseudonym by identifying pairs of addresses that are owned by the same user. Indeed, users tend to reuse the same addresses to carry out their transactions. This makes it possible to map the activities of the different addresses belonging to the same entity by comparing the relationships between these addresses.
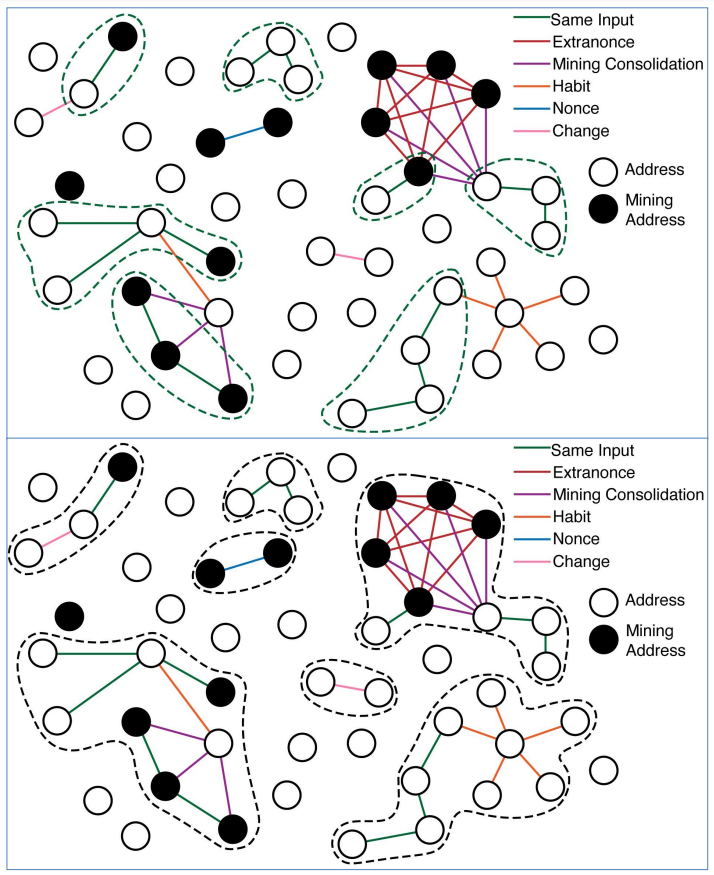
Address Binding on Bitcoin
Source: study by researchers
The connected components in this graph correspond to putative users, since each address of the connected component can be identified with other addresses via a chain of evidence. Chain of evidence which is composed of a wide range of mathematical and cryptographic methods such as address binding. But concretely, what is the point of tracing the actions of different addresses in order to determine whether or not it is a single entity?
For example, in 2018, US Attorney Robert Mueller’s office was able to determine that a group of Russian hackers known as Fancy Bear was responsible for the theft and dissemination of US Democratic National Committee documents by linking them to a target bitcoin address. So if a law enforcement agency determines a user’s identity on the network, they can de-pseudonymize almost any bitcoin address linked to the user’s address. This “follow-the-money” strategy could be used by a dishonest entity to compromise the privacy of all bitcoin users. Yes, because the researchers point out that, on Bitcoin, the more entities we know that hide behind addresses, the easier it is to know new ones by making links between addresses and transactions.
Mainly thanks to the aforementioned methods, the researchers were able to trace almost all operations, both transactional and mining, on the Bitcoin network between 2009 and 2011. They were able to draw the following conclusion: 64 actors, a good part of whom been identified, almost mined most bitcoins (2,676,800 BTC) between 2009 and 2011.
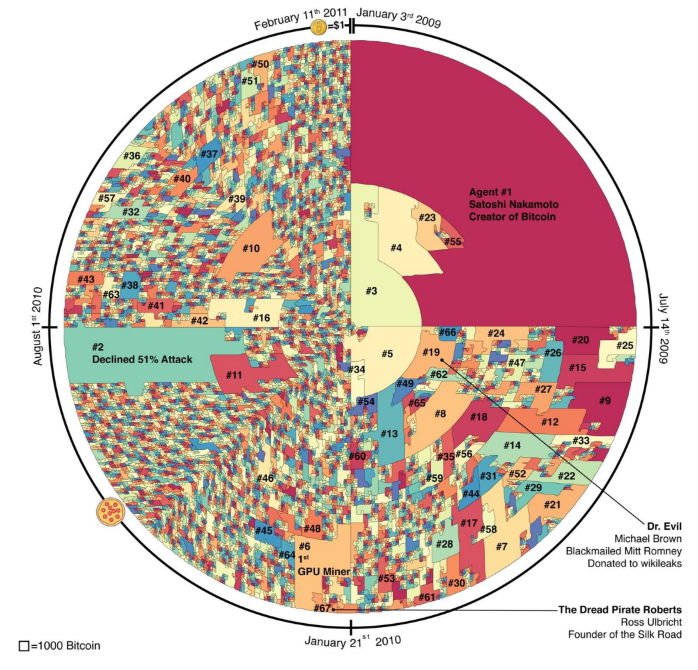
64 agents mined the most bitcoins between the launch of the
bitcoin and when it reached price parity with the US dollar.
Source: study by researchers
The researchers explain that short paths in the network can introduce vulnerabilities in the privacy of Bitcoin users, by making it easier to “follow-the-money” from a known node through a network. chain of transactions involving intermediate users. This makes it possible to determine the identity of a target address. The researchers went even further, beyond determining these transactions, in analyzing Satoshi Nakamoto’s activity using off-chain metadata.
Below, the researchers show Satoshi Nakamoto’s activity by date and time. This graph shows the date and time of known activity by Satoshi Nakamoto, including the UTC (Coordinated Universal Time) timestamp of emails sent to Mike Hearn (dark green), Hal Finney (light green), server Cryptography list server (mustard) where bitcoin was first announced, and the bitcoin list server created soon after (neon green). It also includes the timestamp of Satoshi’s posts on the bitcointalk.org forum (purple) and Sourceforge code commits (grey). All of these activities suggest that Satoshi is awake at these specific times.
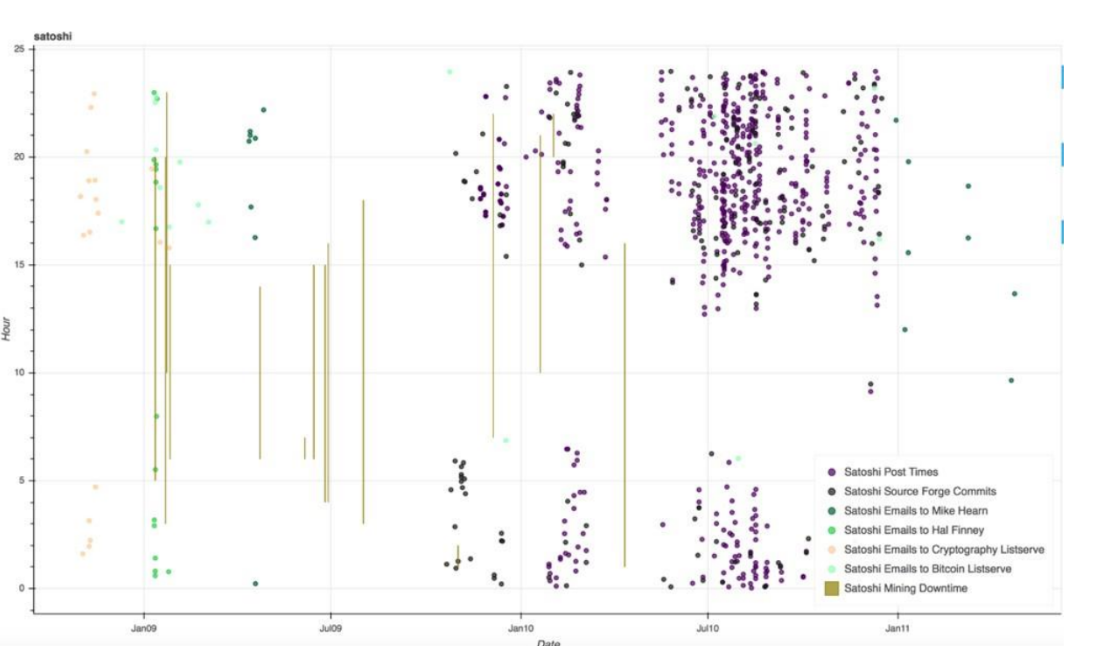
Satoshi Nakamoto activity by date and time (2009-2011)
Source: study by researchers
I let you imagine the strike force that a dishonest entity could have if it decided to follow the actions of a user on the Bitcoin network with the methods of American researchers. Especially if that dark entity already has off-chain data on their target.
Ultimately, it is therefore to a dialectic of invisibility and traceability that Bitcoin invites us, to a complex oscillation between, on the one hand, a crypto-anarchist desire to escape all surveillance, and on the other hand, to the exhaustive visibility of certain data. By eradicating the need for trust (find my article which deals with this notion: Web 3.0, unfailing trust?), favoring the trustless by eliminating uncertainty and making traceability the norm of the network, it reproduces one of the most salient aspects of contemporary ideology: the need for transparency.
A public blockchain, such as Bitcoin, represents such a transparent information system that it presents an ideal situation for an audit. It allows a company to find the data environment at a past time, being certain that it has not been falsified in the meantime. Under these conditions, it is the very idea of secrecy that becomes mysterious within Bitcoin. Does being invisible, or believing oneself invisible, or unidentifiable for certain centralized and institutional authorities mean really evolving in a secret setting?
“When you encrypt private data and make it public, you can’t assume it will stay private forever. Drop by drop, information leakage is eroding once impenetrable blocks, sculpting a new landscape of socio-economic data”. Alyssa Blackburn, lead researcher of the study Cooperation between an anonymous group protected by Bitcoin during the failures of decentralization
