Internet access may currently be disrupted for Fritzbox users who have activated encrypted DNS communication to protect their privacy and use a DNS resolver from Cloudflare for this purpose.
The symptom: Devices that are connected to such Fritz boxes and use the Fritz box for DNS resolution cannot reach destinations on the Internet (devices that use a resolver other than the one in the Fritz box do not have such a problem).
The trigger: The resolver entered in the DNS-over-TLS configuration of the Fritzbox cloudflare-dns.com is currently not responding to DNS requests. With some Fritz boxes, the DNS resolution then fails completely, even if other resolvers are entered that work correctly.
A user reports that he solved the problem by switching off the certificate check. While this improves the reliability of the DNS service, the Fritzbox cannot ensure that it is actually sending its DNS queries to the configured resolver (or to one that only pretends to be the configured one). This can be done in environments with low requirements for the security of DNS responses. The “Allow fallback to unencrypted name resolution on the Internet” function will help just as well. Then the box automatically switches to conventional DNS communication in plain text if the encrypted communication fails for whatever reason.
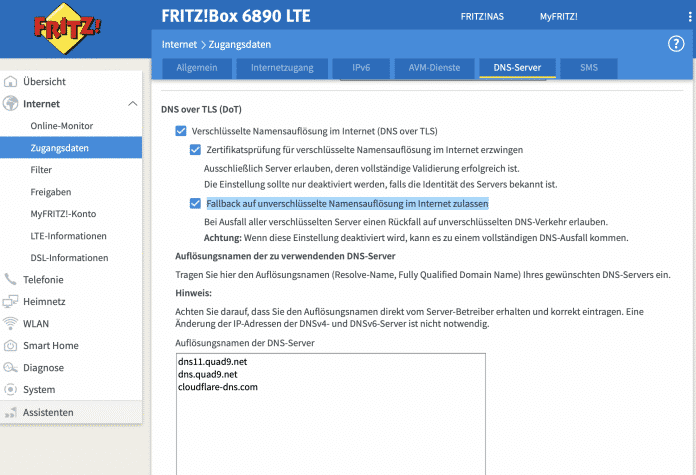
The “Allow fallback to unencrypted name resolution on the Internet” function can be found in the FritzOS interface under Internet > Access data > DNS server.
(Image: AVM)
Remedy: If you continue to value encrypted and trustworthy DNS communication, you should not switch off the certificate check and also not allow a fallback to unencrypted DNS communication. The easiest way to get around this is to delete the currently silent DNS resolver from the list. After that, DNS resolution should work smoothly again. The Fritzbox may need a restart to get itself back on its feet.
Cloudflare’s problem is likely to be temporary. We have notified the company and asked for comment. There are various lists of publicly accessible resolvers circulating on the Internet that can be entered instead of the Cloudflare resolver. The list of DNS privacy developers who are working on standardizing the technology is recommended.
Fast resolver check
If you later want to enter the Cloudflare resolver again, it is advisable to check it first. This can be done with the OpenSSL command, for example:
echo | openssl s_client -connect 'example.com:853'
Example.com is the domain of the resolver you want to check (e.g. dns11.quad9.net), 853 is the port number on which DNS-over-TLS resolvers usually respond. If the resolver responds, the command should return the server certificate. Otherwise OpenSSL reports “operation timed out” after a while.
However, this is only a rough connection test at the TLS level and not a complete functional test. Linux, BSD and Mac users can use the kdig tool to resolve specific domain names. kdig is part of the toolbox knot-dnsutils, which can be installed with common package managers (e.g. apt or homebrew). Here’s how to test whether a resolver resolves DNS queries:
kdig @example.com ct.de +tls
Example.com means the domain of the resolver you want to check (e.g. cloudflare-dns.com). This is followed by the name of a domain that you want the resolver to resolve (e.g. ct.de). With the +tls switch you can set kdig to communicate with the resolver using TLS encryption. If the resolver works, it should return 193.99.144.80 for ct.de.

(dz)

