February 30, 2023, 12:00 CET — The news spread like wildfire. Threads multiply on Twitter to present the evidence on chain night events. Crypto-experts are unanimous and present no doubt. Satoshi’s Wallet Nakamoto is empty.
More alarmingly still, he is not the alone. Other movements have just been detected on wallets from the Satoshi era. In particular a certain portfolio belonging to the fire cypherpunk Hal Finneyknown to have received the first bitcoin transaction in history. Panic seizes the market, the volatility of Bitcoin explodes and the exchanges show $14,000. Internet users are beginning to imagine the worst. If the wallet of our late Hal Finney has also been emptied, there can only be two explanations. Either Nakamoto had access to his private key. Either we are witnessing an event of unprecedented scale, not only announcing the death of bitcoin.
In my previous post, I introduced you to the principle of electronic signature and the basic conditions it must meet to allow your authentication on the blockchain as well as Diffie-Hellman key exchange laying the foundations of asymmetric cryptography. Today we are going to dive into the first cryptographic protocol allowing strong electronic signatures, RSA encryption.
But before that, remember, I gave you a slight reprieve on modular mathematics. “This time, you will not escape it” – I let go in a Machiavellian voice behind my keyboard. But don’t worry, it’s quite easy to understand, you do it every day without knowing it!
Modular horology and mathematics
Forget everything you know, from now on, 12 = 0
Last week, I therefore spoke to you about the modular mathematics which was used, in the Diffie-Hellman key exchange, to simplify the calculations that our two interlocutors must make Alice and Bob. However, his involvement in RSA encryption is much more important, because it intervenes directly in encryption and decryption messages between our two speakers, which is why I am going to try to explain it to you.
What would happen if we found out that 12 ≡ 0 ?
(I use here the triple equals sign for mathematical rigor. Yes, it is not the symbol ofEthereum although it is very close, understand here simply 12 = 0. The triple equals sign will be used as soon as we talk about an equality in a modular system).
Spoiler, this would upset the way we calculate, but you already experience this every day!
For the mathematicians among you, this should remind you of the trigonometric circle. On this circle 2π is equal to 0, likewise for 4π, 6π, etc. It is the same for our clocks, 5 p.m. is also equal to 5am. Modular mathematics comes down to winding the line of all the numbers around a circle according to a predefined cycle. 12 in the example of our clocks. They say we’re in a math modulo 12.
What are the advantages for cryptography?
” Ok Lightnings, that’s very good, but what application in cryptography? I still don’t see the connection » you will tell me.
Patience, I’m coming! In the Diffie-Hellman key exchange, we were performing calculations with of the powers of gigantic numberhere is what happens when we apply a math modulo 12.
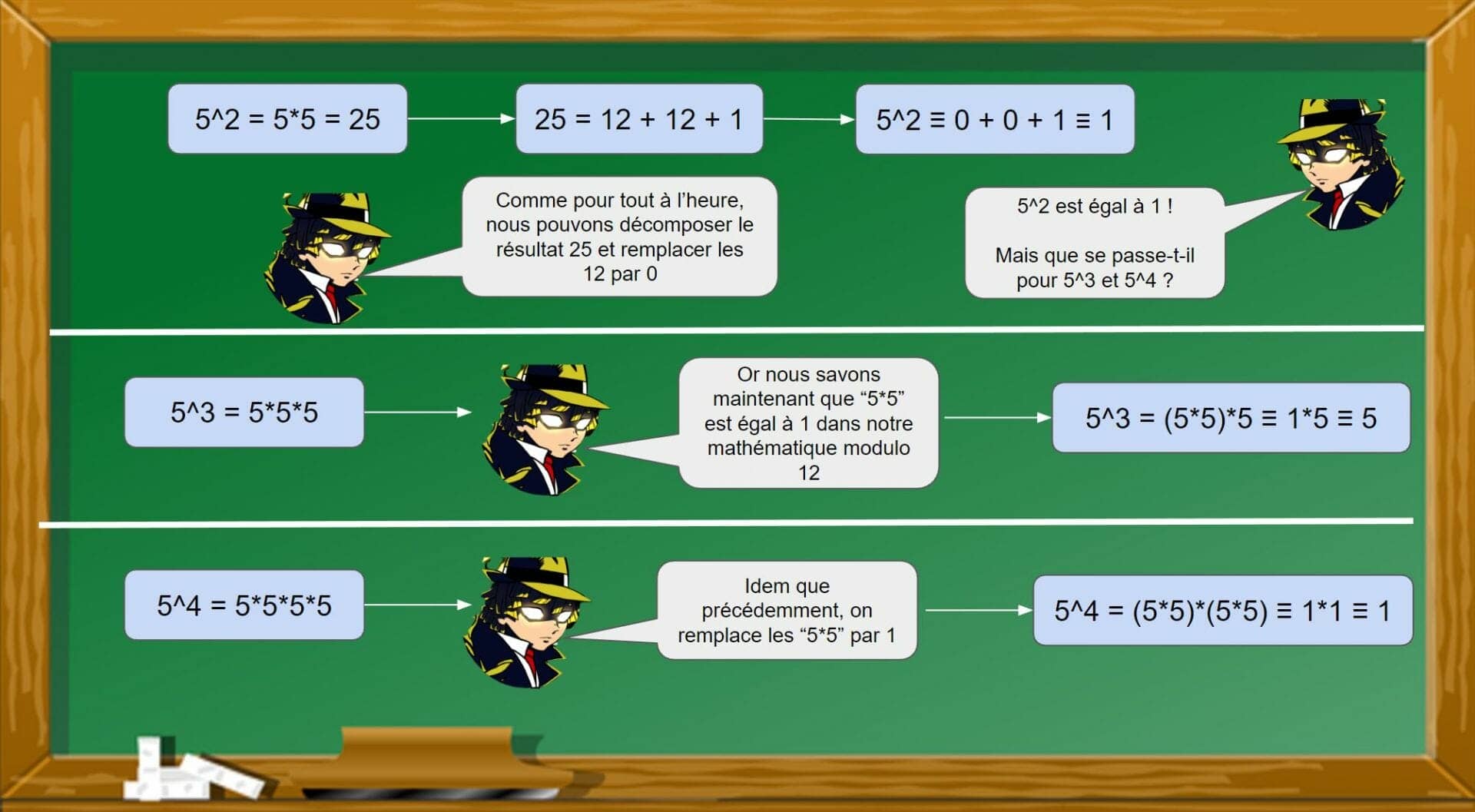
Do you see what this will entail? Mathematics modulo 12 allows us to simplify 5^2 by 1. From this calculation, we can simplify any power of 5:
- For any even power: 5^(even number) will be equal to 1,
- For any odd power: 5^(odd number) will be equal to 5.
It is this little mathematical sleight of hand that makes it possible to use power functions with cryptographically large numbers. Small test to check if you understood the logic:
In a math modulo 12, what is the result of 5^974896232?
We will write the result like this: 5^974896232 ≡ 1 (mod 12) — with mod for modulo.
Easy right? (yes, I’m totally trying to convince myself that my explanations have been clear.) Now that modular math is no longer a barbaric word for you, we can move on to RSA encryption. Hang in there, because this is going to be the hardest part of my crypto series!
>> Prefer to keep your cryptos safe? Choose a Ledger wallet (commercial link) <<
RSA encryption
Construction of public and private keys
RSA encryption, named after the initials of its three inventors, Ronald Rivest, Adi Shamir and Leonard Adelman, uses asymmetric cryptography based on the work of Diffie-Hellman. Where the Diffie-Hellman key exchange only allows the creation of an encryption key without prior unencrypted agreementthe RSA protocol goes further by directly allowing exchange of information via public key encryption. The RSA protocol introduces trapdoor functions.
They have the same properties as one-way functions explained in my previous postapart from the fact that they have what is called a “backdoor », a number allowing the reversibility of the encryption function.
Alice and Bob, always them, want to exchange and sign a document and have never interacted in the past. Alice will create a key pair, a private key which will be used by Alice to sign Bob’s document, and a public keywhich will be used to verify that the signature really comes from Alice.
(Beforehand, don’t bother too much with the mathematical details in red if you have trouble understanding them. Just remember the logic).
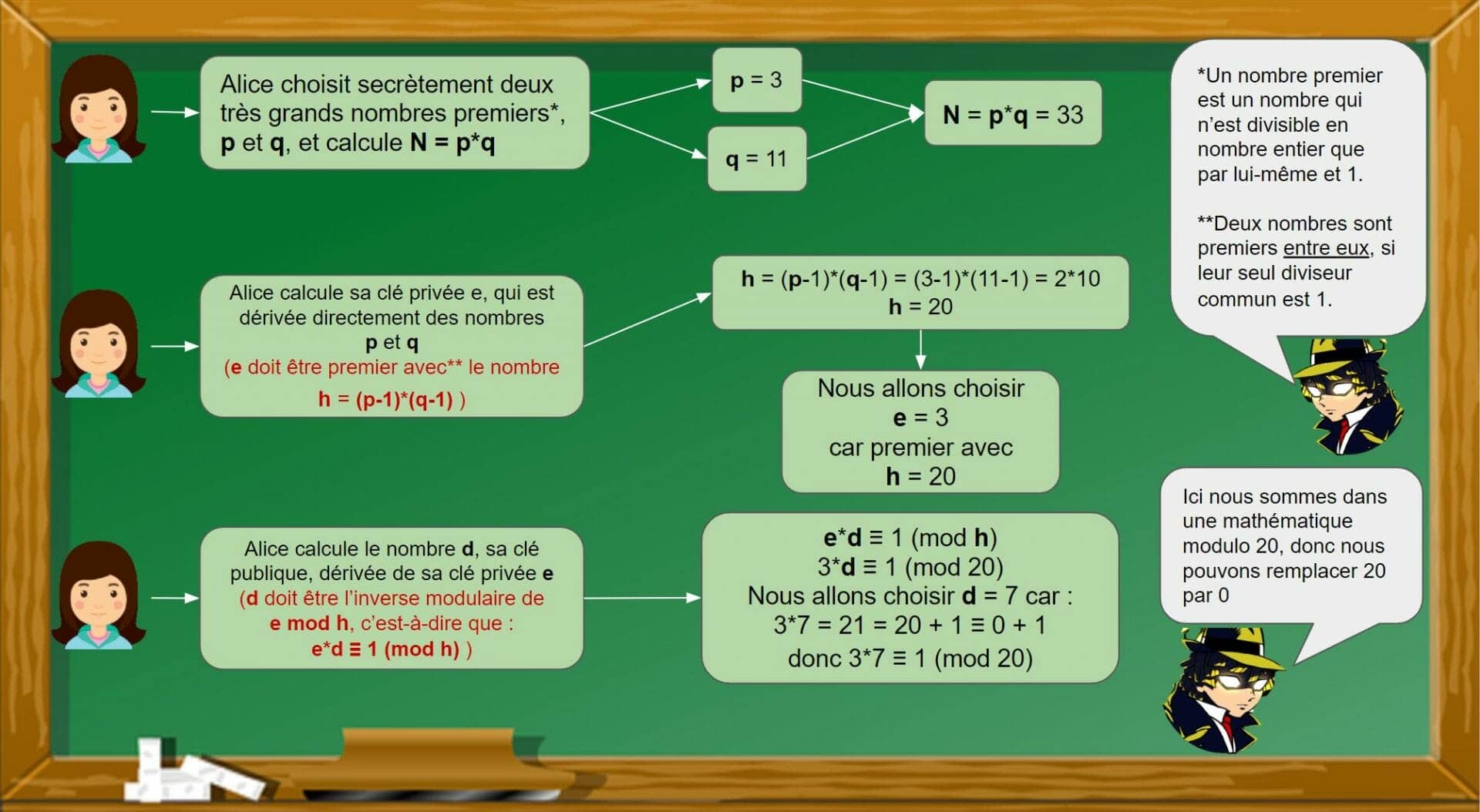
Alice therefore has three numbers in her possession. The public number NOTits public key d and its private key e. These are all calculated using the numbers p and q that she must absolutely destroy so as not to compromise his private key!
This is where the modular math explained above will work its magic:
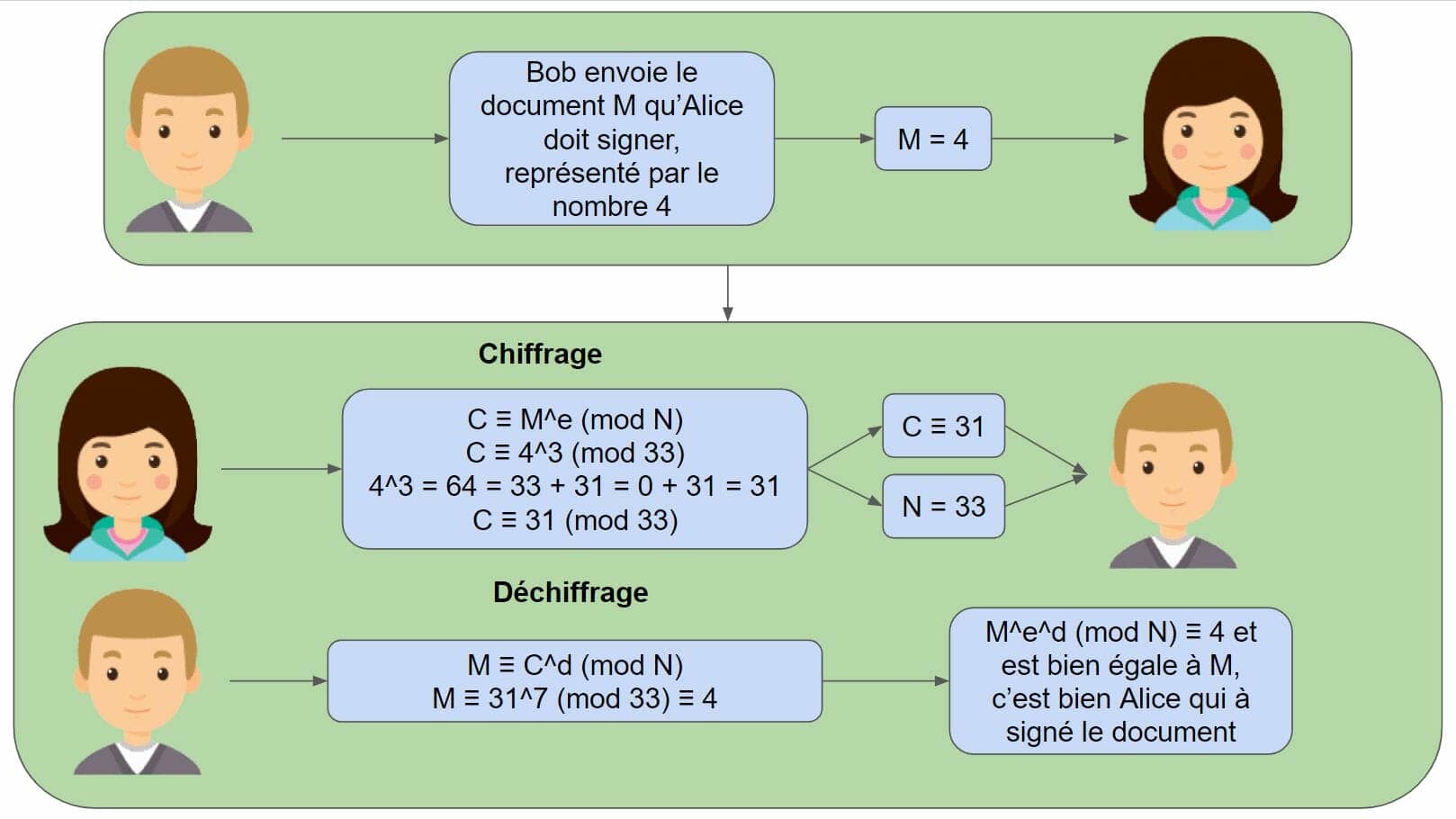
- Bob wants to sign a document M at Alice.
- Alice perform the calculation: C = M^e mod N and send the result VSwhich represents his signature, and the number NOT at Bob.
- Bob perform the calculation: C^d (mod N) that is M^e^d (mod N). If thanks to this calculation Bob finds the document M as he sent it to Alice. Is that’Alice signed it with his private key.
Thanks to our modular mathematics, we therefore have in summary, encryption by Alice’s private key and decryption by her public key :
(Document) ^ (Alice’s private key) ^ (Alice’s public key) = Document
If you remember the property of the “power functions” presented last time, the reverse is totally possible. But it is not equivalentbecause nothing will allow Alice to be sure that it is Bob who sent him the encrypted document, since it is encrypted with his public key. Whether Bob wants to keep the document secret, he will have to encrypt it first with its own private key.
During an electronic signature, encryption by private key and decryption by public key will always be preferred.
Strength and ownership of RSA encryption
The robustness of this encryption comes from the impossibility for a third party to find Alice’s private key only through public numbers NOT, VS and d in a reasonable time. This comes from the complexity, and the unreasonably long computation time, necessary to achieve prime factorization public number NOT in order to find p and q. A number that would allow Alice’s private key to be easily found by brute force.
Today, we know how to find this decomposition by “brute force” with numbers of 795 bit. But commonly used RSA keys are 2048 bit, which still leaves us a little leeway. However, some doubts hover because of a quantum algorithm being able to break RSA relatively easily, Shor’s algorithm.
To return to the electronic signature, here, Bob challenges Alice to sign the document M with his private key, if he cannot find the document M identically via verification using Alice’s public key. It’s not Alice who signed the document! The signature therefore meets all the criteria mentioned in the previous article, namely:
Authenticity : Alice is authenticated by her private key, which she alone possesses.
Tamper-evident : Alice’s private key is mathematically tamper-proof, because it is protected by the impossibility of carrying out a decomposition into prime factors.
Non-reusability : Signature VS is unique because it is derived from Alice’s document and private key.
Inalterability : Signature VS serves as evidence as it is derived from the document itself. If the document is modified, Alice will only have to sign it again and show that her signature is different from the previous one.
Irrevocability : The rules above being respected, Alice cannot deny her signature.
Enough convoluted formulas for today, I can feel your eyes growing heavy after all those mathematical pirouettes. Next time we’ll go dig Bitcoin and the big boss of encryption protocols, the ECDSA protocolthen we will end on the hash and its role in proof of work !
February 30, 2023, 4:00 p.m. CET With sweaty palms, sweat on their brows, crypto experts are doing all they can to try to clear up the situation. They review all the mathematical concepts and cryptography protocols in search of a flaw, a detail, which would have gone unnoticed for more than fifty years. While the answer must be hidden there, before their eyes, the incomprehension pushes the accusations to be made more and more against Google and China, overwhelmed with having used their quantum computer in order to send Bitcoin beyond the grave. The noose is tightening, but this enigma remains, for the moment, still unfathomable. Its resolution is unfortunately not yet within reach of our comprehension.
In crypto, do not economize on caution! So, to keep your crypto assets safe, the best solution is still a personal hardware wallet. At Ledger, there is something for all profiles and all cryptos. Do not wait to put your capital in safety (commercial link)!
