Encrypt files and folders per container
VeraCrypt is a classic when it comes to data security and is less complicated to use than some users might think. The tool is equipped with professional functions.
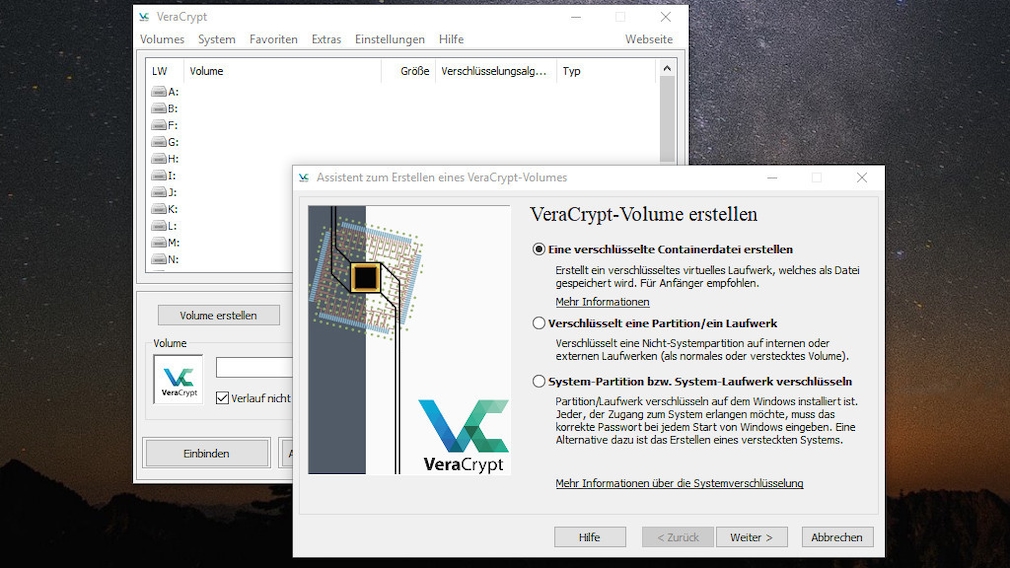
If you want to protect individual files or folders from unauthorized access, this is suitable VeraCrypt. It is the successor to the proven TrueCrypt, which was discontinued in 2014. VeraCrypt is said to be more secure than its predecessor in important areas. The service is comparable. At first, VeraCrypt looks like a professional program and it really is: The operation requires some training, then you can easily use a wizard to create protected container files – without a file extension – (which integrate themselves as virtual drives in the Explorer and similar to folders files record and provide). You can also secure the system start with VeraCrypt: Windows then only starts after you have entered the password you previously specified. An advantage of VeraCrypt is the open source approach – thanks to open source, the working method is comprehensible.
the Portable version of VeraCrypt does not master the boot protection, so use the version to be installed for the full range of functions. Incidentally, the installable VeraCrypt version comes with a portable mode, the system start encryption is not provided here either. For starters, it’s a good idea to only create container files. You determine their file system. If you move a file or folder to the container drive in Explorer, you have encrypted the content.
Download VeraCrypt Portable
Protect folders – Encryption made easy
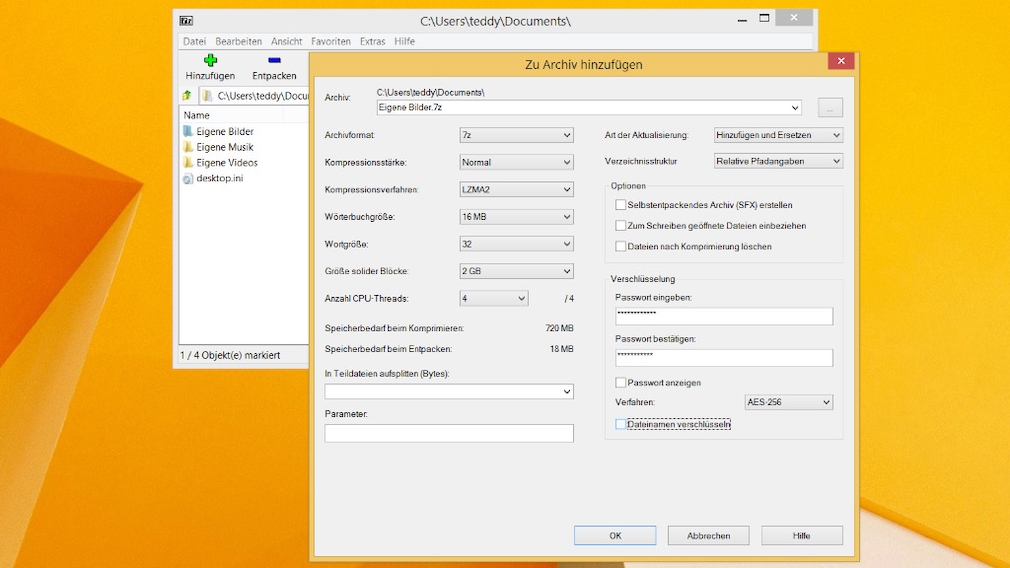
Putting a password on files using a zip tool may be a makeshift solution. On the other hand, such programs are lightweight and usually easy to use.
Download 7-Zip (64-bit).
Download 7-Zip Portable
Download WinRAR (64-bit).
Encrypt individual files
Probably the simplest special tool for encryption is EasyCrypt. It is easy to use, since the interface essentially only has the two buttons “Encrypt” and “Decrypt”. For comparison: VeraCrypt uses an AES-256 algorithm by default and creates containers that, like folders (but only after entering a password), make the files hidden in them accessible. Unlike VeraCrypt, with EasyCrypt no alternative algorithm can be selected, the tool always uses AES 256 bit. When encrypting, EasyCrypt creates a protected counterpart for each encrypted file .aes-name extension. The content is initially unusable, but can be brought back to life with EasyCrypt: the tool opens the decrypted file if desired and/or deletes the encrypted counterpart.
Secure and encrypt data
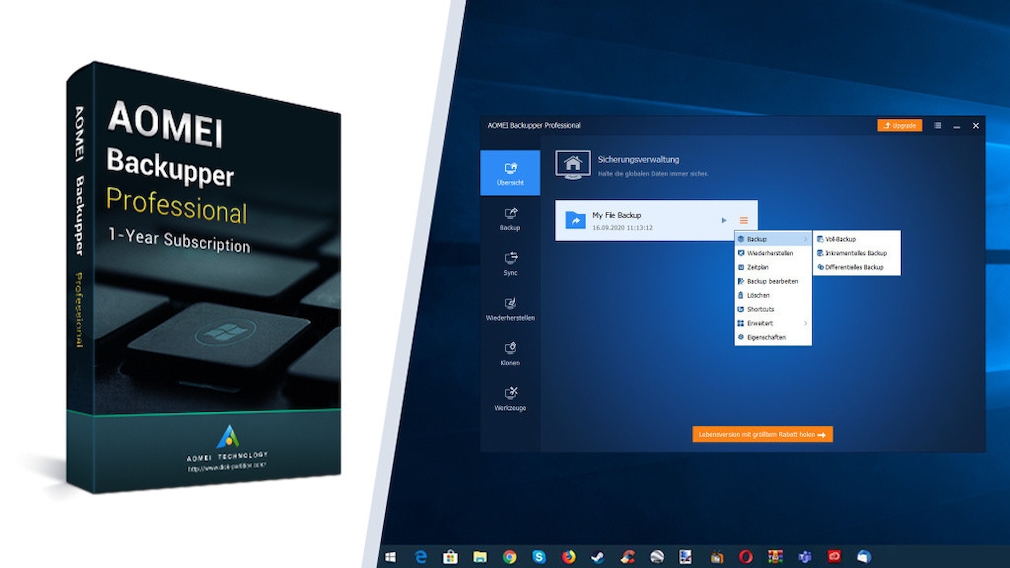
The AOMEI Backupper is already great in the freeware version, the Pro version goes one better.
Regular data backups are a necessary and sensible evil – they protect you from losing your drive contents if, for example, the hard drive fails. Check your backup tool to see if it offers encryption and use it. The AOMEI Backupper is one of the recommended backup programs – but does not encrypt in the free version. Of the Aomei Backupper Pro Edition does this very well: The software actually costs money, here you can get it as a free full version. Among other things, you can use this to create complete backups of your operating system using an image. If you switch on password protection, recovery is only possible with a password. So data thieves cannot simply reconstruct your completely duplicated working environment including operating system, settings, programs and files. Note that backup tools only offer encryption as an extra, but don’t make it their main purpose. If you want to protect files well, you should use two applications for reasons of convenience: one for backups (possibly activate password protection here), one for encryption.
AOMEI Backupper Pro – Download Free Full Version for 1 Year
How does encryption work?
A few explanations of the basics, how encryption tools work and how they are handled: There are various algorithms for making file content inaccessible, such as AES, which is considered to be secure or provides good protection – with different bit lengths. Encryption also goes by the name of encryption and changes the way data is processed. The user first starts his encryption software and tells it the file to be saved, which is done with an Open button.
In his encryption software, the person concerned usually defines a password that he uses together with an encryption algorithm. Depending on the program, several techniques are available, for example the protection method can be selected via a drop-down menu. The encryption tool writes a new file to disk – in a format that differs from the original file, and therefore with a different extension. Sometimes the protection software deletes the original file, if not, you should take care of it. Because the encrypted file is only a copy, the original remains, it is stored in plain text and without full encryption of the Windows partition (password prompt when booting) a feast for data thieves. Sometimes encryptors offer instead of creating the new file as a self-extracting EXE file in a special format (the advantage is that opening with a password works without the original application, so you can uninstall it without hesitation or give the file to someone else without the pass on the software; however, self-extracting EXE files will require more memory).
A distinction is made between symmetric and asymmetric encryption: With the former, users and software deal with just one password. It is used for encryption and decryption. The second variant uses a separate password for both; this is more complex and is mainly used for e-mail encryption.

