Image: Google.
DDoS attacks (distributed denial of service attacks) are probably the least sophisticated cyberattacks, but they can still cause great damage. Today, Google and other major cloud companies spotted and reported the largest DDoS attack on record.
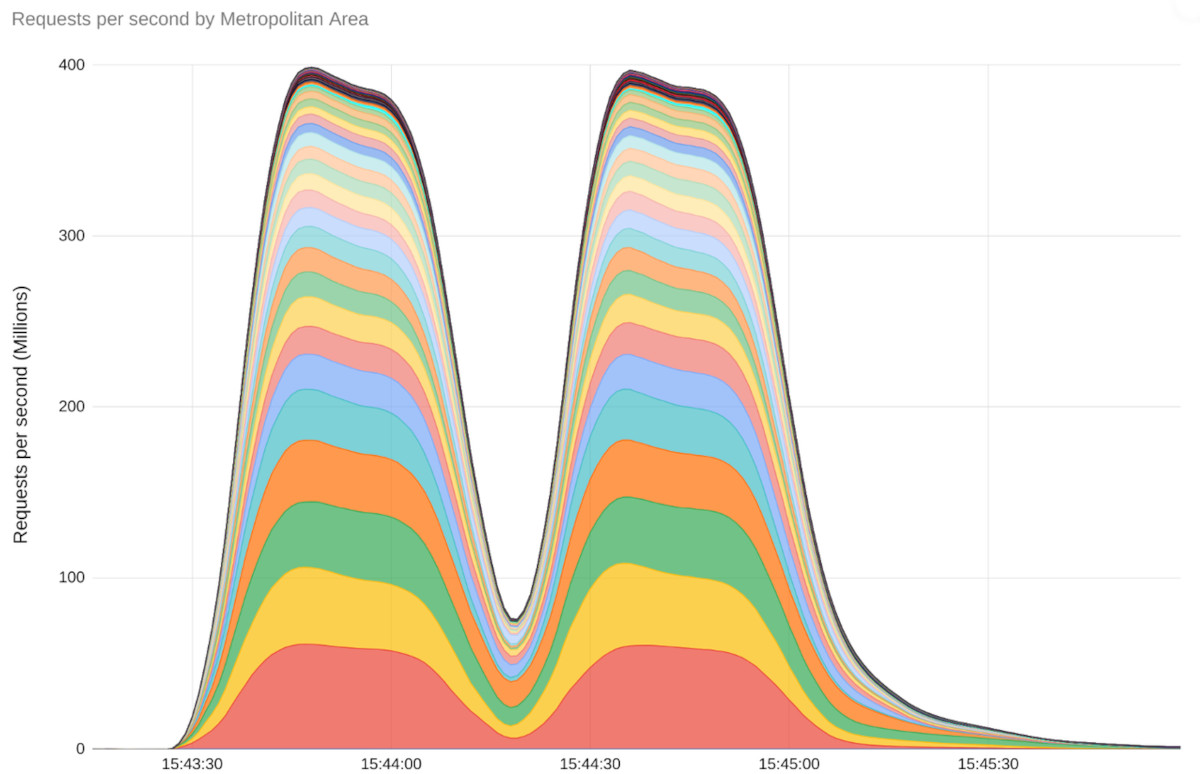
Last August, Google Cloud was hit by the largest DDoS attack in history. The digital assault had then reached the unprecedented figure of 398 million requests per second (RPS). To understand the magnitude of this figure, Google explains that this means that Google Cloud received more requests per second than Wikipedia during the entire month of September 2023.
In other words, it’s huge. The attack on Google Cloud, which used a new technique – called “fast reset” – was 7.5 times larger than all previously recorded DDoS attacks. In 2022, the “largest DDos attack ever recorded” reached “only” 46 million RPS.
A coordinated response
Google is not the only one to have been affected. Cloudflare, a leading Content Delivery Network (CDN), and Amazon Web Services (AWS), the world’s largest cloud service provider, also reported being attacked. Cloudflare repelled a 201 million RPS attack, while AWS withstood a 155 million RPS attack.
These DDoS attacks, which target major infrastructure providers, began at the end of August and are “continuing today,” according to Google. Despite the scale and intensity of these attacks, major technology companies’ global load balancing and DDoS mitigation infrastructure was able to effectively counter the threat and ensure uninterrupted service to their customers. .
In the wake of these attacks, companies coordinated a cross-industry response, sharing information and mitigation strategies with other cloud providers and software maintainers. This collaborative effort resulted in patches and mitigation techniques that most major infrastructure providers have already adopted.
Rapid Reset
The so-called “Rapid Reset” technique exploits the stream multiplexing feature of the HTTP/2 protocol, which constitutes the last step in the evolution of Layer 7 attacks. This attack works by pushing multiple logical connections to be multiplexed over a single HTTP session.
This is an “upgrade” of HTTP 1.x functionality, in which each HTTP session was logically distinct. So, as the name suggests, an HTTP/2 fast reset attack consists of multiple HTTP/2 connections with requests and resets one after the other. If you have implemented the HTTP/2 protocol for your website or internet services, you are a potential target.
In practice, the fast reset attack involves transmitting a series of requests for multiple flows, followed immediately by a reset for each request. The targeted system will analyze and act on each request, generating logs for a request that is then reset or canceled. Thus, the targeted system wastes time and money generating these logs, even if no network data is sent back to the attacker. A malicious actor can abuse this process by issuing a massive volume of HTTP/2 requests, overwhelming the targeted system.
This is actually an accelerated version of a very old type of attack: the DDoS attack by flooding HTTP requests. Defending against these types of attacks requires implementing an architecture that helps specifically detect unwanted requests and adapt to absorb and block these malicious HTTP requests.
The vulnerability exploited by the attackers has been identified as CVE-2023-44487.
How to protect yourself from it?
Organizations and individuals using HTTP-based workloads over the internet are advised to review the security of their servers and apply vendor patches for CVE-2023-44487 to mitigate similar attacks. Fixes are in progress. But until they are installed on a large scale, other Rapid Reset attacks are likely to take place.
Most companies do not have the resources to deal with such attacks. To be able to repel them would require extensive and powerful DDoS defense services, such as Amazon CloudFront, AWS Shield, Google Cloud Armor or CloudFlare Magic Transit.
This attack will eventually be patched, but in the meantime, similar attacks will occur, probably very soon. Remember, “security is not a product, it is a process”.
Source: ZDNet.com