Google’s “OSS-Fuzz” project for testing open source software can now also search for errors from the Log4j Java library in projects. The vulnerability in the widely used logging library for Java applications is currently vulnerable and will likely remain until the affected systems are patched. The zero-day vulnerability, discovered just over a week ago, is listed as CVE 2021-44228 and [Update 18.12.21, 13:30: soll mit der von der Apache Foundation veröffentlichten Log4j-Version 2.17.0 behoben worden sein. Version 2.16.0 begegnete dem Problem nur teilweise, schützte aber nicht vor unkontrollierter Rekursion durch selbstreferenzielle Lookups.]
OSS-Fuzz is a free service presented in 2016 for testing open source projects using fuzzing – a method in which the software to be tested is fed consciously or accidentally incorrect input data. This can reveal potentially slipping errors such as buffer overflows, which can lead to crashes. OSS-Fuzz is currently used by more than 500 critical open source projects, as Google writes in its security blog.
Integration of Jazzer should help
As part of a partnership announced in March with the German company Code Intelligence, which specializes in fuzz testing, Google is testing an integration of Jazzer in OSS-Fuzz. This means that fuzzing is also possible via JVM (Java Virtual Machine) applications for weak points. In this context, Code Intelligence has improved its jazzer fuzzing engine so that it can detect remote JNDI lookups.
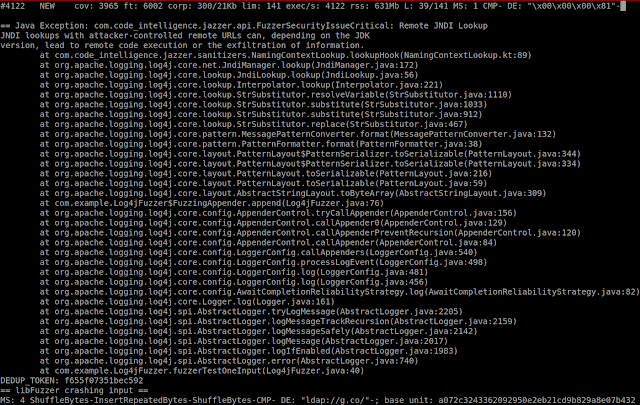
OSS-Fuzz and Jazzer find Log4Shell vulnerabilities
(Image: Google)
“Vulnerabilities like Log4Shell are an eye-opener for new attack opportunities for the industry. With OSS-Fuzz and Jazzer we can now detect these types of vulnerabilities so that they can be fixed before they become a problem in the production code,” says Jonathan Metzman of Google Open Source Security Team.
Last year, Google said it invested more than ten billion dollars in cybersecurity measures and supported third-party vendors with $ 100 million to fix vulnerabilities.

Apache developers also list possible steps to secure the server in a security message. The information provided by Log4j is updated daily, most recently on December 17th.
(mack)
