While Google is struggling to remove illegal download sites from its search results, hackers have found a way to make them appear anyway. The technique is called “SEO poisoning”, and it tricks the biggest search engine in a relatively simple process. Explanations.
With its status as a gigantic web directory, Google also has a responsibility not to promote illicit activities. However, the matter is far from easy when download sites regain popularity and that some of them are just a front for hackers. Google therefore regularly removes these platforms which contain a number of malware, but must face fierce opposition from the latter.
And they have more than one string to their bow to circumvent the web giant’s restrictions. One of the most popular methods is called ” SEO poisoning“. The idea is simple, but formidable. To select its results, Google analyzes, among other things, the number of times a page is used as a link on another site. Concretely, the more a page is cited, the higher it appears in the results.
Related: Google Takes Down Vast Hacker Network That Infected Over 1 Million Windows PCs
Hackers take on Google at its own game to promote their sites
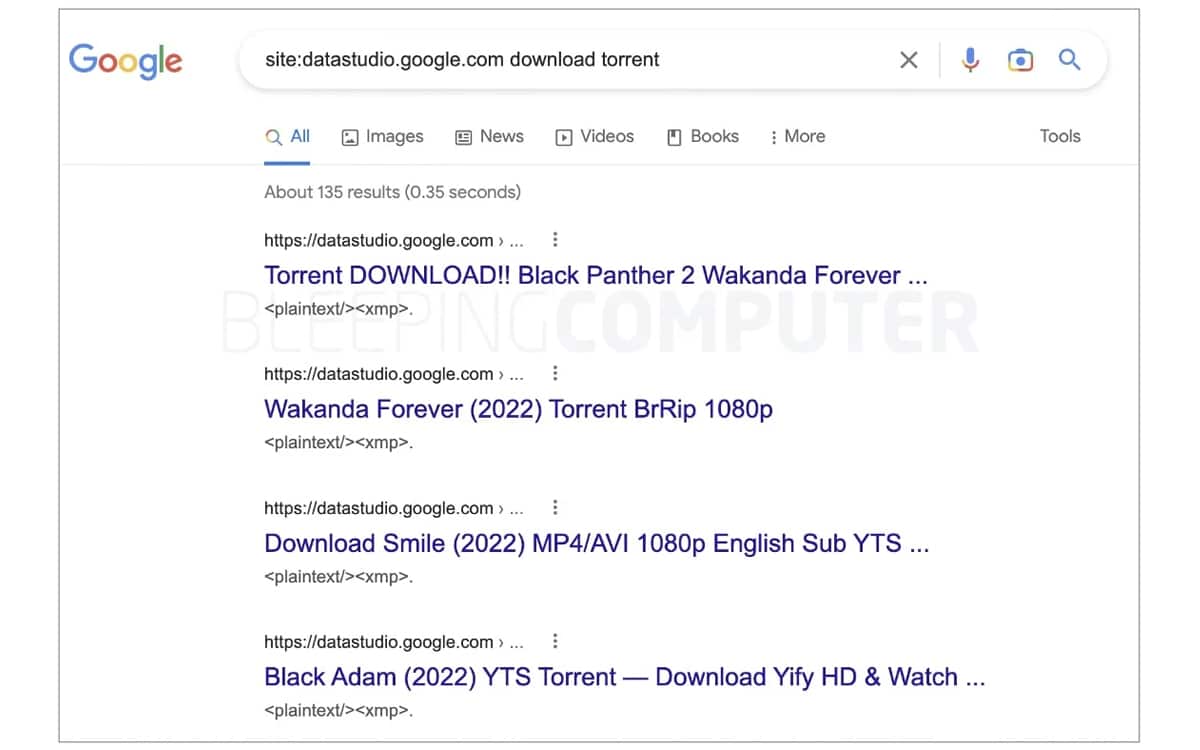
Therefore, it is therefore enough for hackers to stuff certain “legitimate” sites with links to their own platforms. As our colleagues at Bleeping Computer have discovered, one of these most recent campaigns even attacks a domain name belonging to Google, namely datastudio.google.com . By typing the latter in the search bar followed by the keywords “download” and “torrent”, these are dozens of illegal download sites that appear in the results.
Problem, these sites are usually not even regular torrent platforms, but rather fronts for hackers who use them tomass-distribute their malware.While unlucky users think they are downloading the trending movie of the moment, they are actually exposing themselves to serious security risks. We therefore advise you to be particularly vigilant if you wish to visit one of these sites.
Source: Bleeping Computer