The researchers of Bitdefender have just revealed the presence of a backdoor operating on macOS systems. Called RustDoor, this backdoor masquerades as a Visual Studio update and allows hackers to remotely connect to compromised Macs.
Impenetrable, macOS? Not so sure, as evidenced by the recent discovery of malware coded in Rust, Trojan.MAC.RustDoor. Just detected by Bitdefender, the threat would have had free rein for three months, at least. According to the cybersecurity company, RustDoor’s analysis made it possible to highlight the first malicious activities as early as November 2023, and to confirm that the backdoor was still active as of February 2. If Bitdefender has not yet been able to precisely identify the authors of the attack, several elements converge towards the Black Basta and ALPHV/BlackCat groups, renowned ransomware actors.
A discreet backdoor that can affect all architectures
It is a threat that has long gone unnoticed. And for good reason, RustDoor was coded in Rust, whose syntax and semantics differ from other more widespread languages, like C and Python. A feature that makes analysis and detection of malicious code complicated, and which explains why this backdoor has managed to fly under the radar of cybersecurity researchers for so long.
Another specificity of RustDoor: its distribution takes the form of a Visual Studio update (FAT binaries), even though Microsoft will abandon the development of its code editor for Mac next August. Among the suspicious file names, Bitdefender mentions zshrc2, Previewers, VisualStudioUpdater, VisualStudioUpdater_Patch, VisualStudioUpdating, visualstudioupdate And DO_NOT_RUN_ChromeUpdates. To do things right, the hackers also took care to develop an Intel version (x86_64) and an Apple Silicon (AMD) version of their malware, which means that all Macs can potentially be affected.
An operating mode and IoCs that summon the ALPHV/BlackCat spectrum
By tracing RustDoor activity, Bitdefender was able to identify the deployment of three successive Rustdoor variants. The first, called Variant Zero, dates back to November 2, 2023 and seemed to test the functionalities of the backdoor without exploiting them. Three weeks later, Variant 1 included a list of properties describing persistence mechanisms and sandbox escape techniques on macOS.
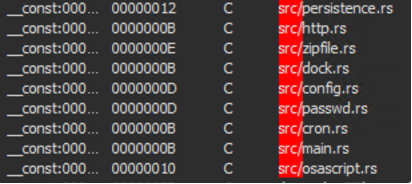
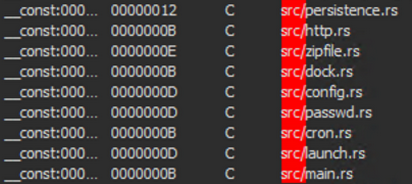

However, we had to wait until November 30 for Variant 2 to appear and make the backdoor fully operational. This augmented version of the malware includes a complex JSON configuration file allowing persistence, as well as an Apple script dedicated to exfiltrating data to command and control servers, also called C&C or C2.
Clearly, between November 2023 and February 2024, RustDoor allowed hackers to remotely take control of compromised macOS systems, modify system configuration files to launch automatically when the Mac boots, and run regular tasks allowing to copy files from the infected computer to a hidden folder, compress it into a ZIP archive and transfer it to a C2 server, neither seen nor known.
Although Bitdefender is currently unable to identify the perpetrators of the attack, the company noted that many elements and indicators of compromise intrinsic to the malware had already been used during ransomware attacks. (also coded in Rust) orchestrated by the Black Basta and ALPHV/BlackCat groups from November 2021, including three of the four C2 servers associated with RustDoor.
See the offer
- Simple interface
- Imperceptible performance impact
- Full Features
Bitdefender Antivirus chooses more minimalist features on Mac compared to the Windows version. Nevertheless, it shines with its almost impeccable efficiency, a very low impact on system performance and a user interface which is perhaps a little too “Windows” for some but which remains simple and discreet. Whether to protect a single Mac or to integrate into a multi-device solution, BitDefender remains a benchmark.
Bitdefender Antivirus chooses more minimalist features on Mac compared to the Windows version. Nevertheless, it shines with its almost impeccable efficiency, a very low impact on system performance and a user interface which is perhaps a little too “Windows” for some but which remains simple and discreet. Whether to protect a single Mac or to integrate into a multi-device solution, BitDefender remains a benchmark.
Source : Bitdefender



0