Image: Kaspersky.
A new cyberattack technique targeting iPhones using iMessages has been disclosed. This method is effective up to iOS 16.2, so iPhone owners simply need to update their device to a newer version to protect themselves from it.
Kaspersky Lab demonstrated the new attack technique, dubbed “Operation Triangulation,” at the 37th Chaos Communication Congress, SiliconAngle revealed.
4 vulnerabilities exploited jointly
The triangulation attack uses a combination of four security vulnerabilities present in the iPhone to bypass hardware security protections. It is also a “zero-click” technique, meaning it can infect a targeted device without requiring any action from a user.
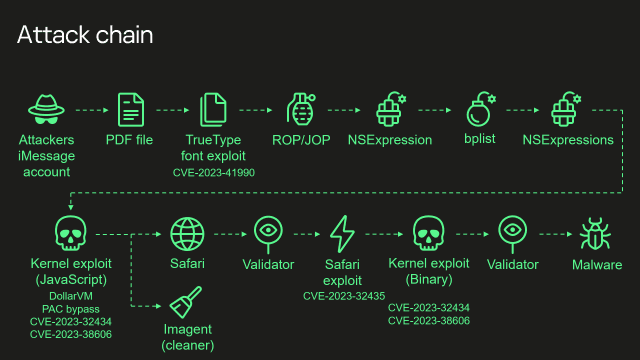
To carry out this new attack, the cyberattackers were able to exploit the vulnerabilities CVE-2023-41990, which concerns a TrueType font file; CVE-2023-32434, a memory control flaw in Apple’s kernel; CVE-2023-32435, a memory management flaw in WebKit; and CVE-2023-38606, which allows an application to modify sensitive kernel state information.
These four security vulnerabilities, already actively exploited, can allow an attacker to breach a device’s data privacy, arbitrarily execute code remotely, and bypass its security policies.
Course of the attack
To carry out their attack, cyberattackers can exploit the vulnerability in the AdAssist TrueType font to distribute attachments containing malicious code to their victims through an iMessage. The iPhone to which the attachment is sent then executes the malicious program without its owner being informed. According to Kaspersky researchers, this security flaw has existed since the early 1990s. It was recently removed by a patch.
Once the malware gains access to a device, it uses the XNU vulnerability to modify the JavaScript core library environment and manipulate memory to gain access to execute core API functions.
The third vulnerability exploited makes it possible to modify the kernel to obtain read and write access to the entire physical memory of the device. The attacker can then also bypass the Page Protection Layer (PPL), which prevents modification of existing code on the iPhone.
At this point, an attacker can do pretty much whatever they want on the device, including running malware. But the attack presented by Kaspersky does not stop there: the attacker can also exploit a vulnerability in Safari to erase all traces of its infiltration.
Ongoing investigation
Additional hardware may have been used to bypass the hardware security of targeted Apple devices. A thorough investigation is underway into how each vulnerability was exploited, according to Apple. Its results are expected to be published next year.
Source: ZDNet.com