It all starts with a simple command line that can, at your expense, steal your personal information.
Hackers no longer need to look very far to create phishing windows… Web browsers under Chromium very simply offer them a solution!
The applications under Chromium in question
Phishing continues to be talked about… and it’s not about to stop. A new way to phish users has just been discovered by the site Mrd0x, which could not be easier for anyone with a basic knowledge of HTML and CSS. Hackers could therefore simply use any application under Chromium to perfectly imitate any popular website. For information, many internet browsers today run under Chromium code such as Google Chrome, Microsoft Edge, Opera or Brave.
L’feat uses the “–app” parameter which can be added to a command line after opening an executable file. In the case of our browsers, –app opens a link in a window in “application” mode, so without a search bar or bookmarks.
With a few more tweaks, it’s very easy for a hacker to change the appearance of this window to look like any site you normally trust, or even a Microsoft application.
Add this as a shortcut to your desktop and you’ll see nothing but fire. See for example how Mrd0x managed to reproduce the Teams login window almost identically:
Windows is not the only victim operating system
Applications on Chromium are not limited to Windows. Thus this flaw is very easily reproducible on any browser mentioned above running on a macOS or Linux system. The command line to execute remains the same and the window is just as customizable.
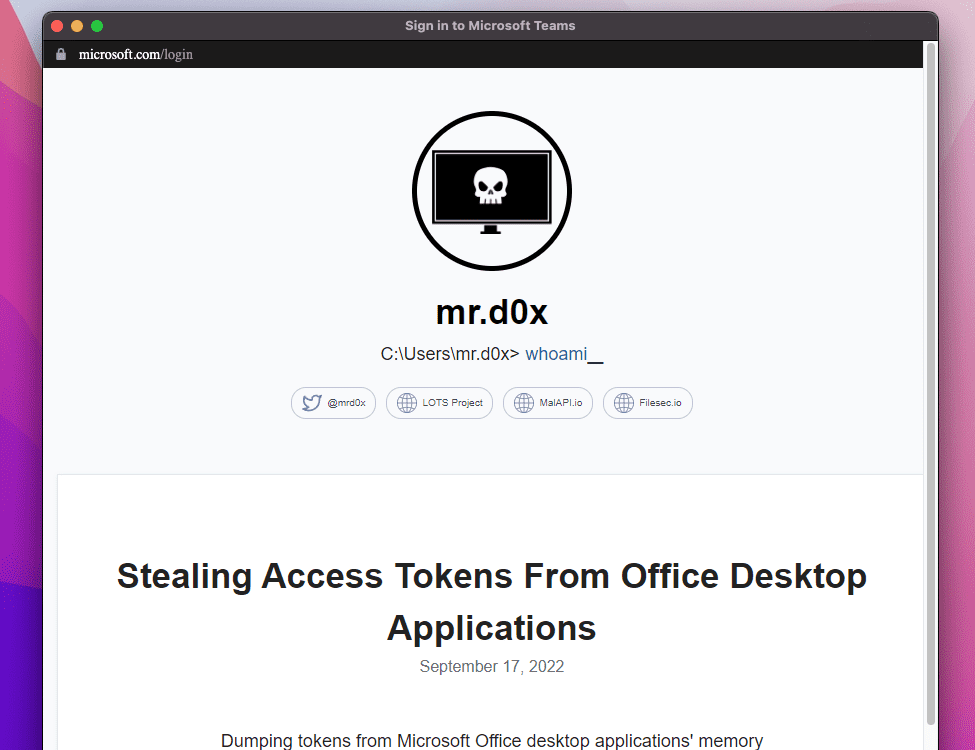
Don’t start doubting the icons on your desktop, though. This feat is only feasible for a hacker who already has a foothold in your network. But always be on guard when downloading from unknown source.
Source : Mrd0x

5