Two very serious vulnerabilities were discovered recently by Google’s Project Zero. They directly affect Android smartphones manufactured by Google and Samsung. The vulnerabilities are both rated as “severe”, which means they must be fixed immediately or you could be at risk.
This may sound hyperbolic, but this time it’s absolutely accurate.
Exynos Chipset Vulnerability
The first major vulnerability (and it is clearly the worst) concerns Exynos modems. In detail, these are four vulnerabilities that can cause serious issues with Exynos hardware such that, even without user interaction, all a hacker would need to know is your smartphone number to create an exploit and compromise it remotely. .
Known devices that are affected by these vulnerabilities include the following:
- Samsung Galaxy S22, M33, M13, M12, A71, A53, A33, A21, A13, A12 and A04.
- Vivo S16, S15, S6, X70, X60, and X30 series.
- Google Pixel 6, 6 Pro, Pixel 6a, Pixel 7 and 7 Pro.
- All wearables that use the Exynos W920 chipset (such as the Galaxy Watch 4 and 5).
- All vehicles that use the Exynos Auto T5123 chipset.
A total of 18 zero-day vulnerabilities have been discovered in Samsung’s Exynos chips, seven of which allow remote code execution.
Google released the March Pixel update to fix these vulnerabilities. The fix was made available for my Pixel 7 Pro over the weekend, but is still not available for my Pixel 6 Pro. It is crucial that anyone with a device listed above checks and applies the update as soon as it is made available for their device.
How to check for an update on a Pixel smartphone?
1: Open Settings
The first thing you need to do is open the Settings app on your phone, which you can do from the “gear” icon in the notification area or from the apps menu.
2: Open System Update
Scroll down to the bottom of the Settings page and tap System. On the System page, tap System updatethen on Check for update. If there is an update for your smartphone, apply it immediately.
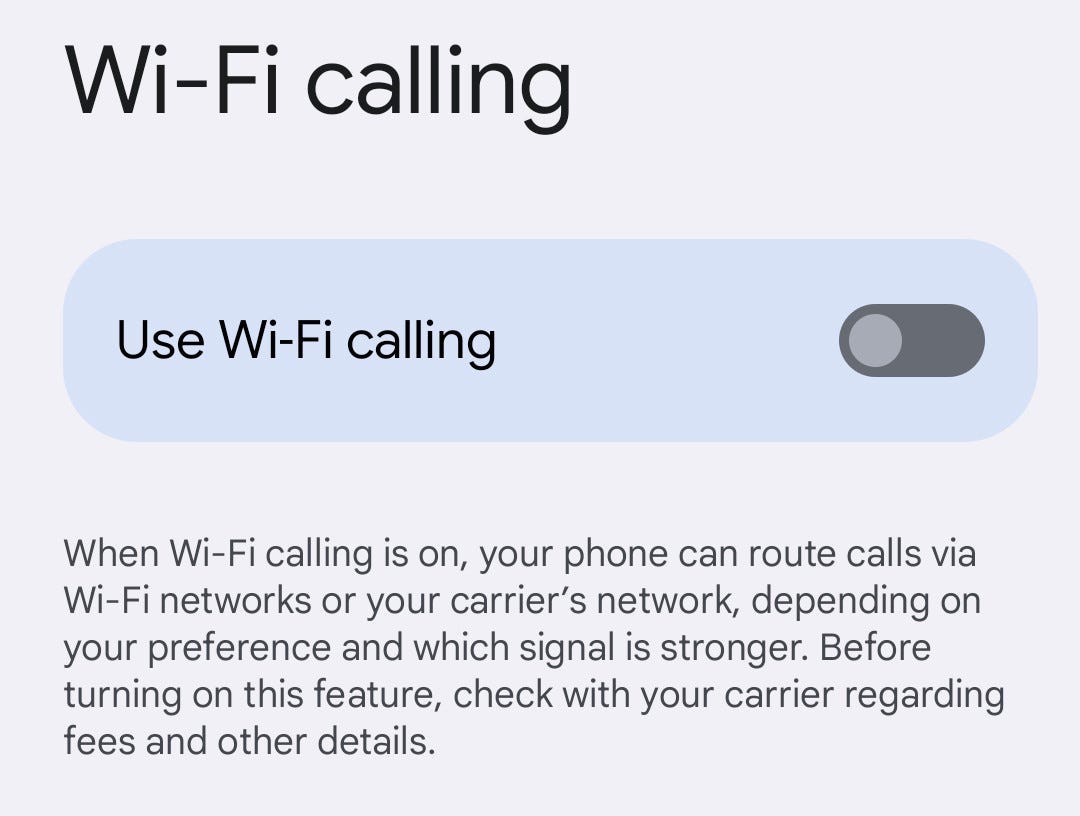
If Wi-Fi Calling is enabled and you haven’t received the update yet, disable Wi-Fi Calling. Image: Jack Wallen
Checking for Updates on Samsung Phones
If you are using an affected Samsung device, remember to go to Settings > Software (or system) updates. If you see the March 1, 2023 security patch listed, you are ready for five of the eighteen vulnerabilities (CVE-2023-26072, CVE-2023-26073, CVE-2023-26074, CVE-2023-26075, CVE-2023-26076). The other vulnerabilities have not yet passed the 90 day deadline and have not been assigned a CVE identifier. Along with the March 1, 2023 update, Samsung updated its advisories to remove the Exynos W920 SoC as an affected chip.
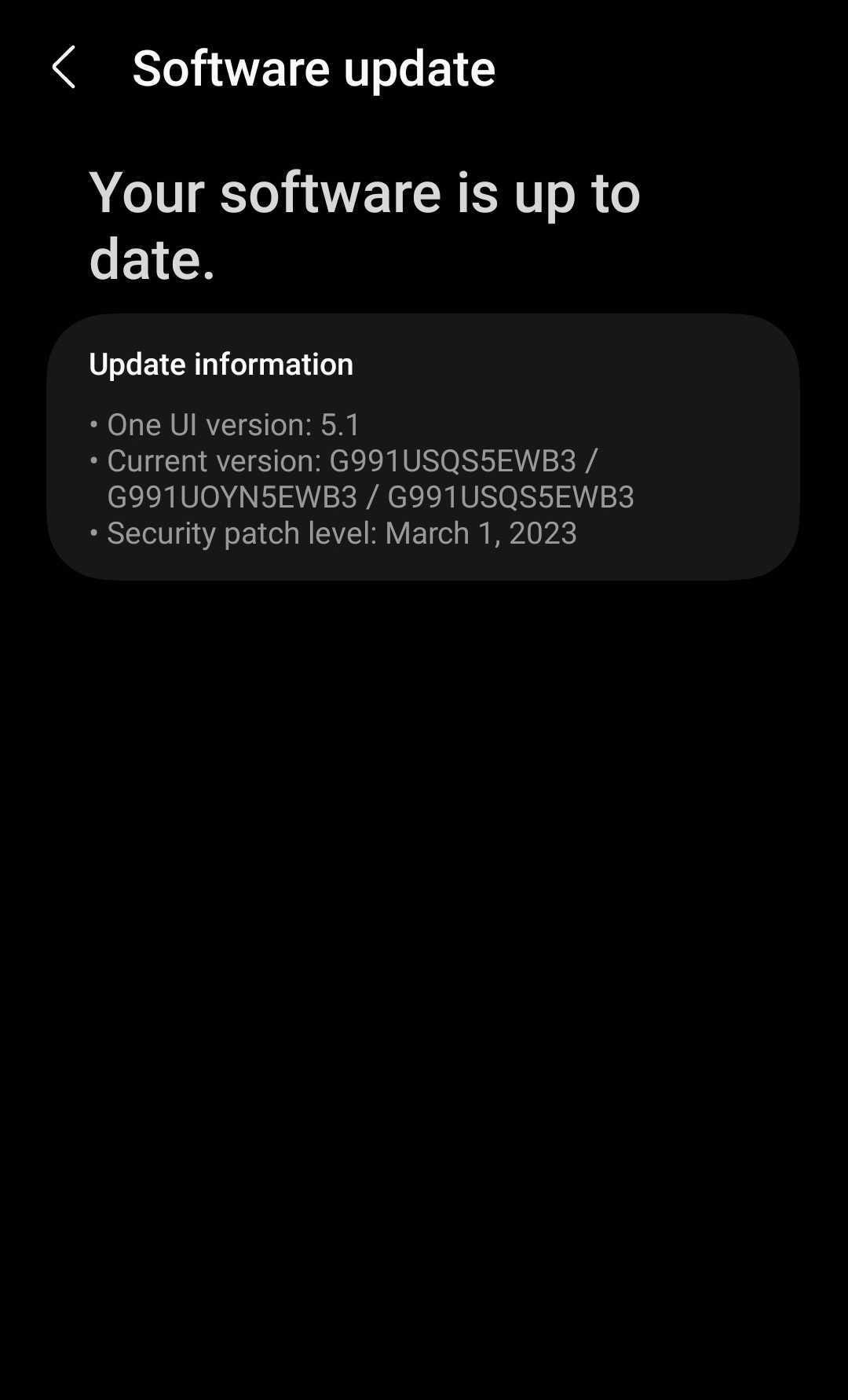
Samsung smartphones must have the March 2023 security patch installed to be safe from the Exynos vulnerability. Image: Alyson Windsor/ZDNET
What to do if your smartphone has not yet received the update?
If your phone hasn’t received the update yet, you need to disable VoLTE and Wi-FI calling. To do this, go to Settings > Network & Internet > SIMs & Wi-Fi Calling. Be sure to tap the ON/OFF slider for Use Wi-Fi Calling until it is in the off position.
Markup tool for screenshots on Pixel
The other serious vulnerability was found in the Markup utility of the Pixel phone. It allows hackers to de-reference and crop edited screenshots taken on the device. If you take a lot of screenshots (especially those that contain sensitive information), this vulnerability should be taken seriously. For example, you can share a screenshot containing bank account information. You could redact sensitive information before sharing it. With this vulnerability, a hacker could reveal this sensitive information and use it against you.
Screenshots shared via services that compress and decompress images (like Twitter) are not vulnerable. But it’s not a risk worth taking.
Fortunately, Google fixed this flaw in the March security update.
However, even with the patch, any screenshot taken before the update will still be vulnerable. That’s why I suggest you delete any screenshots (from phone and cloud) that contain sensitive information (whether you’ve redacted it or not).
If your Pixel or Samsung smartphone has not yet received patches for either of these vulnerabilities, I strongly recommend that you check daily until the update arrives and apply it as soon as possible. ‘she comes.
Source: “ZDNet.com”