Microsoft’s cyber defense cell has detected a cyber espionage campaign launched by Russian hackers, linked to the Kremlin. The latter used the professional social network LinkedIn as well as spoofed email addresses to deceive the victims.
This is an almost ordinary hacker technique. A group of criminals from Russia carried out a cyber espionage campaign by creating fake LinkedIn profiles in order to get in touch with their target. The operation was spotted and detailed in a report from Microsoft’s Threat Intelligence Center, published on August 15, 2022.
Seaborgium, a group of hackers also known as ColdRiver, is suspected of acting on behalf of the Kremlin. They mainly target organizations and leaders in NATO member countries to steal confidential information. This time, the Russian hackers created a myriad of fake social media profiles and email addresses to chat with their targets. These are from from the world of intelligence, defense as well as non-governmental organizations (NGOs) and intergovernmental organizations says Microsoft.
Information collected without the knowledge of the victims
Using these profiles, the malefactors start a conversation and gain the trust of the victims until they send them an attachment. The latter is generally a pretext analysis report and requires entering login credentials and email address to access it. Microsoft indicates that the attackers managed to impersonate employees of a company to send these messages internally in the group.
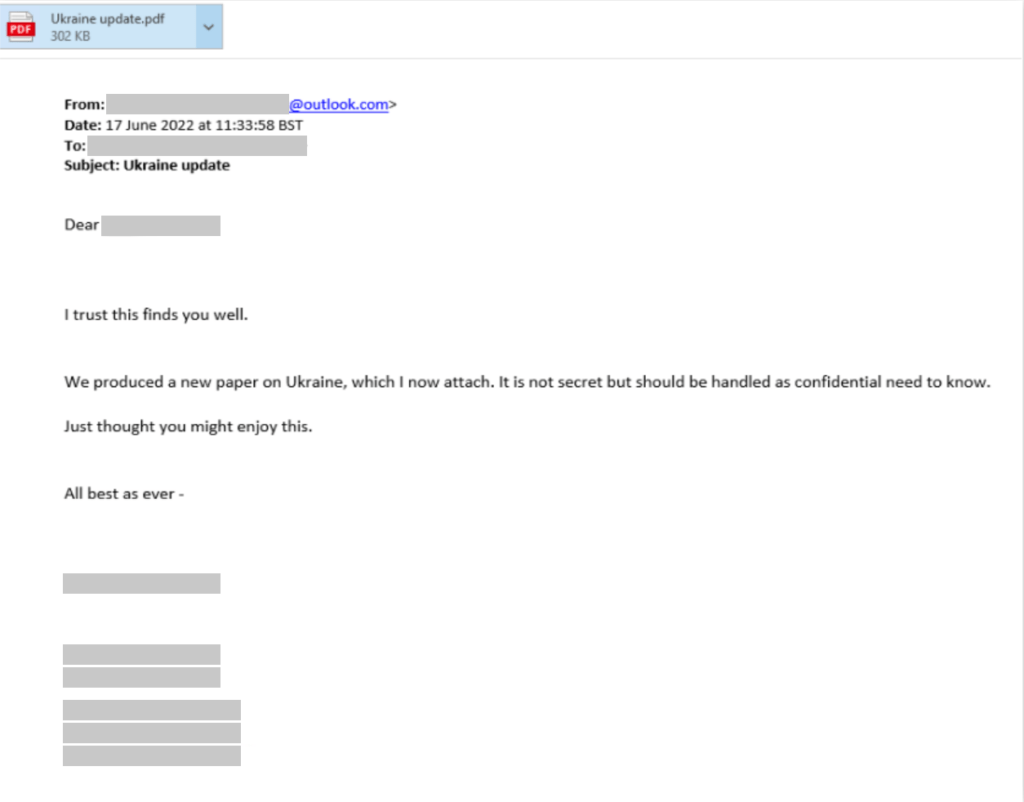
Seaborgium would use EvilGinx, a computer tool that acts as a proxy, intercepting information between the victim and the site’s server. Thus, the criminals received the double authentication data and were able to circumvent this security barrier.
The tech giant shared and blocked sixty-nine domain names associated with the phishing campaign. The same method had been used to trap British politicians, the emails had then been published on a conspiratorial site created especially by the group of Russian hackers.
Fake LinkedIn profiles are also a technique of North Korean hackers, so be careful who contacts you on this network.

