The number of decentralized finance (DeFi) and blockchain projects has grown massively over the past year, but their increased popularity has also sparked the interest of cyberattackers – who have managed to steal at least $1.8 billion in 2021.
Blockchain is a digital ledger technology that records transactions in such a way that it is difficult to alter or modify it. Therefore, these technologies have enormous potential for managing cryptocurrency assets and transactions, as well as facilitating smart contracts, finance, and legal agreements.
In recent years, the blockchain has enabled the emergence of decentralized finance. DeFi financial products and systems are an alternative to traditional banks and financial services, relying on decentralized technologies and smart contracts to operate.
DeFi, NFTs and cryptocurrencies are now popular targets for malicious actors, who take advantage of vulnerabilities, logic errors and programming flaws – as well as phishing campaigns to steal victims’ digital funds.
In May, Microsoft introduced the term “cryware” to the Standard Dictionary of Digital Threats. This new term describes malware designed to harvest and steal information from unhosted cryptocurrency wallets. These wallets are hosted directly by users and not by a third party, which makes them attractive to attackers.
On Tuesday, cybersecurity researchers at Bishop Fox published an analysis of top thefts of blockchain and DeFi applications in 2021. The cybersecurity firm estimates total losses at $1.8 billion.
The team looked at 65 major ‘events’, 90% of which were considered ‘unsophisticated attacks’.
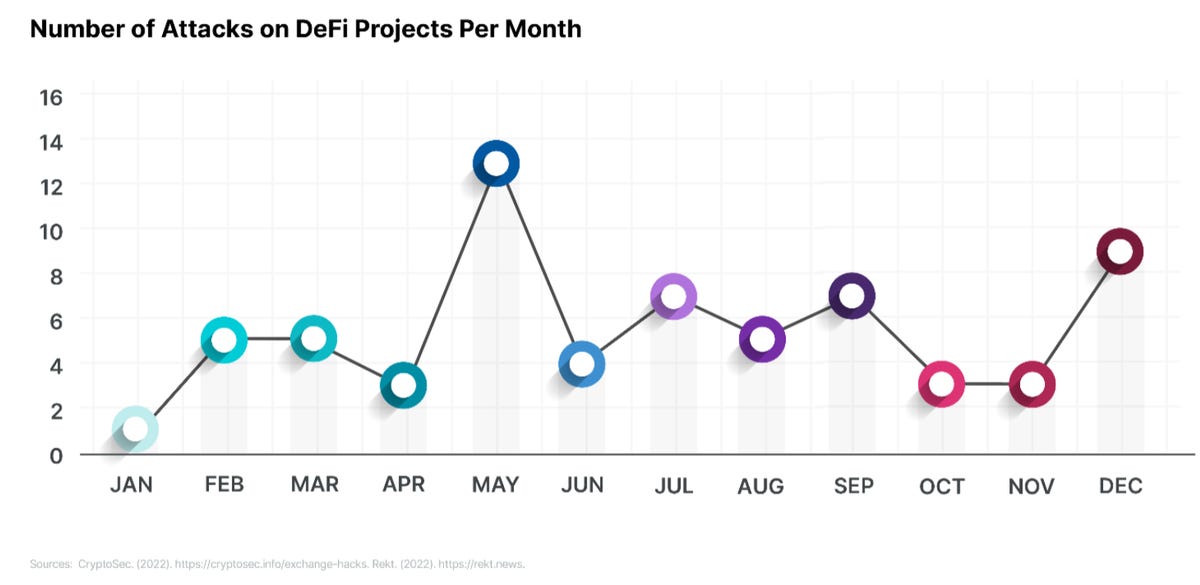
Source: Bishop Fox | CryptoSec.
According to the researchers, DeFi projects suffered an average of five major cyberattacks per month, with peaks in May and December.
The main attack vectors in 2021 were:
- 51% of vulnerabilities in smart contracts;
- 18% protocol and design flaws;
- 10% compromise of wallets;
- 6% scams (exit scam);
- 4% distribution of private keys;
- 4% service front-end hacks;
- 3% arbitration;
- 2% bugs related to cryptocurrencies;
- 2% front runs (transactions queued with knowledge of future trades).
“We can see that in most cases the attack originated from a vulnerability in the smart contracts or in the logic of the protocol itself,” the researchers note. “It’s not surprising for a recent technology that may lack a certain technical perspective on the implementation of security measures. »
When it comes to the types of vulnerabilities exploited in smart contracts, the most common issues exploited by malicious actors are known bugs, vulnerabilities contained in forks, and sophisticated attacks. “Rug pulls” (the creator of the project gives up while keeping investors’ money) and other “exit scams” (the administrators of an exchange close their service and keep the cryptoassets deposited by users on their platform) have also been recorded to a lesser extent.
However, many of these attacks could be avoided with robust audits and testing before going into production. Developers using forks should also regularly check their codebases for any security issues impacting the source code of a DeFi project.
“We can say without hesitation that DeFi is currently a target that attracts thieves looking for big and fast gains,” says Bishop Fox. “This observation is obvious given the youth of this technology and the fact that it’s all about the money. »
“Few advances and technological developments have never encountered problems. In the same way that the first computers were networked without really considering the possibility of spreading a virus, DeFi developers tend to seek innovation in their algorithms more than protection. »
Source: ZDNet.com
