To bypass the protections of Android 13 and 14, hackers are doubling their ingenuity with increasingly sophisticated malware. New example with Chameleon, which simply disables your fingerprint reader.
Sometimes, the ingenuity of hackers can command respect, as long as their actions do not directly affect us. Always on the lookout for new techniques to steal your data, hackers redouble their efforts with each operating system update to bypass security barriers.
This is again the case here with an Android malware called Chameleon which uses techniques never before seen to steal the sensitive data of its victims, in particular their banking information.
A malware that hides its game well
Appearing for the first time in January 2023 in Australia and Poland, the Chameleon malware has apparently evolved according to the cybersecurity research institute ThreatFabric (via Bleeding Computer). This then pretended to be local banks and injected false interfaces to then infect users and thus steal their access codes.
But Android has evolved, particularly since version 13. Google’s system now blocks permissions deemed dangerous which could be modified by unsavory applications. It is therefore more complicated for hackers to monitor the activity of their victims to steal their sensitive information.
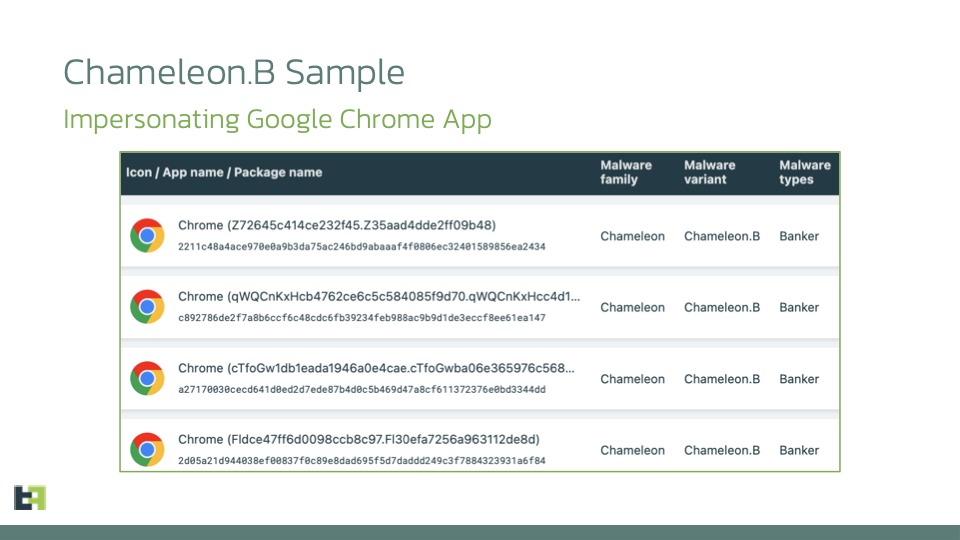
This new version of Chameleon cleverly circumvents the problem by piggybacking on a legitimate application like Google Chrome, installed via an .APK file. Google’s browser is the same as the one on the Google Play Store, but it is infected with malware that can do whatever it wants with it.
Disable the fingerprint sensor remotely
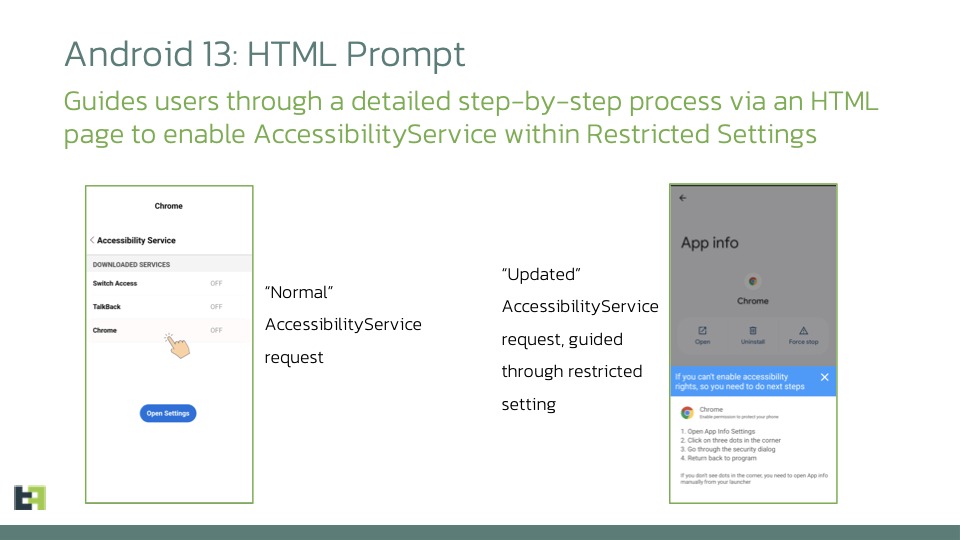
Thus, the fake browser, undetectable by Google’s protections, displays an HTML page explaining to the user how to activate the accessibility services necessary for the malware to operate.
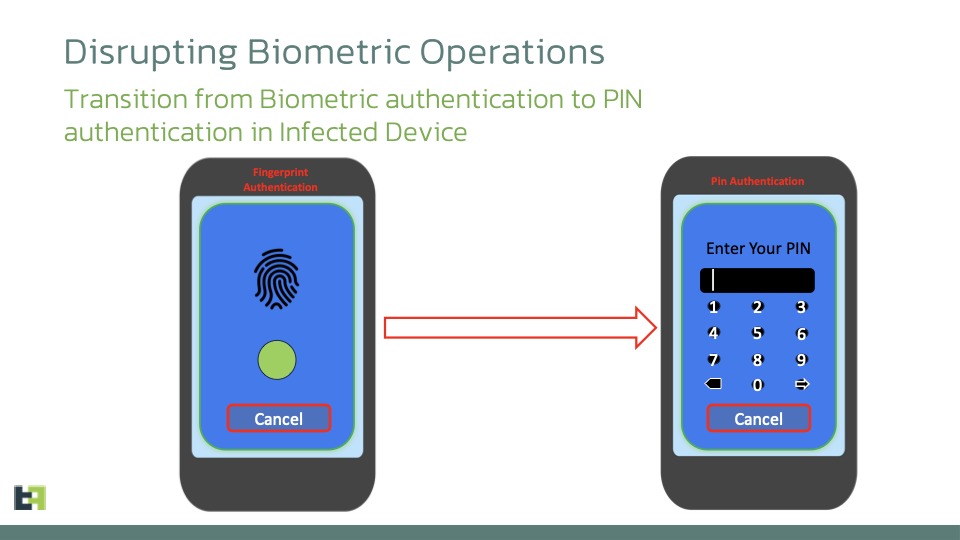
Worse still, the program can deactivate the various biometric unlocking options, such as fingerprint or Face Unlock, in order to force the user to use their PIN code. This will thus be stolen by the pirates via a keyloggerwhich saves all actions performed on the screen.
As the Bleeding Computer site points out, this malware is spread via questionable .APK files, so we advise you to install these applications if you are certain that they come from reliable sources, such as alternative App Stores for Android.
We also advise you to use the Google Play Protect function, which regularly scans your applications and permissions to detect any unusual behavior.
