A VPN everyone knows roughly what it’s for, but no one really knows how to explain how it works. What is behind this tool that allows you to strengthen the security of your internet browsing? And how to use it? We will explain everything to you.
Abbreviation for Virtual Private Network, the VPN, as we understand it for the general public, is an online technical device that is responsible for securing your browsing by encrypting a certain amount of your data. Initially designed to create secure access to company servers for employees, this tool has now been democratized and adapted so that everyone can benefit from enhanced security on the Internet.
The nerve center of the action, the VPN server has a decisive role since it is thanks to it that your IP address is hidden and that you can “relocate” your internet connection. Simply put, by installing a VPN on your computer or smartphone, you:
- Install a VPN client that will use an encrypted connection protocol (the famous tunnel)
- which will connect to a remote VPN server
- And this server will then serve as a source of data for browsing or downloading on the Internet.
The principle of the VPN server is therefore to be a source of delocalized internet data, which makes it possible to hide its real IP, from your ISP or third parties, just like your connection information, but also to deport its internet connection in another country, if the VPN server is located in another country.
The data that then circulates on this VPN server is sent and encrypted after passing through the VPN tunnel to your computer or smartphone.
The offer of consumer VPNs is also very wide and to find your way around, you can consult our VPN comparator.
Web security exists
We often tend to think that using a VPN is the only way to protect your internet connection and improve the confidentiality of your data circulating on the web. Let’s break this received idea right away: no, surfing the internet is not a permanent danger. And yes, your browsing is secure most of the time.
Making purchases, communicating personal information is safe as long as you stay within the fold of sites using the https protocol. A protocol that has become widespread since 2015, when Google began to penalize sites that did not use it.
The VPN, an additional layer of security
However, if this https protocol applies encryption to your data (which is sufficient for 95% of uses), it is not able to secure all of it. This is particularly the case for your IP address or your connection time. When you connect to a public network, for example, the risk of your data leaking increases. This is where using a VPN comes in to provide an extra layer of security.
How ? By using an encryption protocol that is specific to it and sometimes proprietary (NordLynx, OpenVPN, WireGuard, etc.) and which makes it possible to dig a “VPN tunnel” making all of your activities much more difficult to trace.
This VPN tunnel is useful in several scenarios:
- apply an extra layer of security when connecting to less secure networks;
- through its encryption, it protects the data that circulates between your device and the VPN server;
- at the end of this tunnel, your data lands on the VPN server, most of whose providers guarantee a strict privacy policy for user data (VPN with no activity log kept).
How does it work ?
But in reality and without going into a myriad of technical details, how does the VPN provider ensure that your information will not be visible to anyone?
To explain it, the How Stuff Works site uses a nice analogy. You have to imagine the internet as an ocean and the sites as a myriad of small islands. To get to these islands, you can use your internet service provider’s ferry company. It’s friendly, reassuring, but you are traveling in a group and some passengers who are too curious or malicious may observe you during this trip.
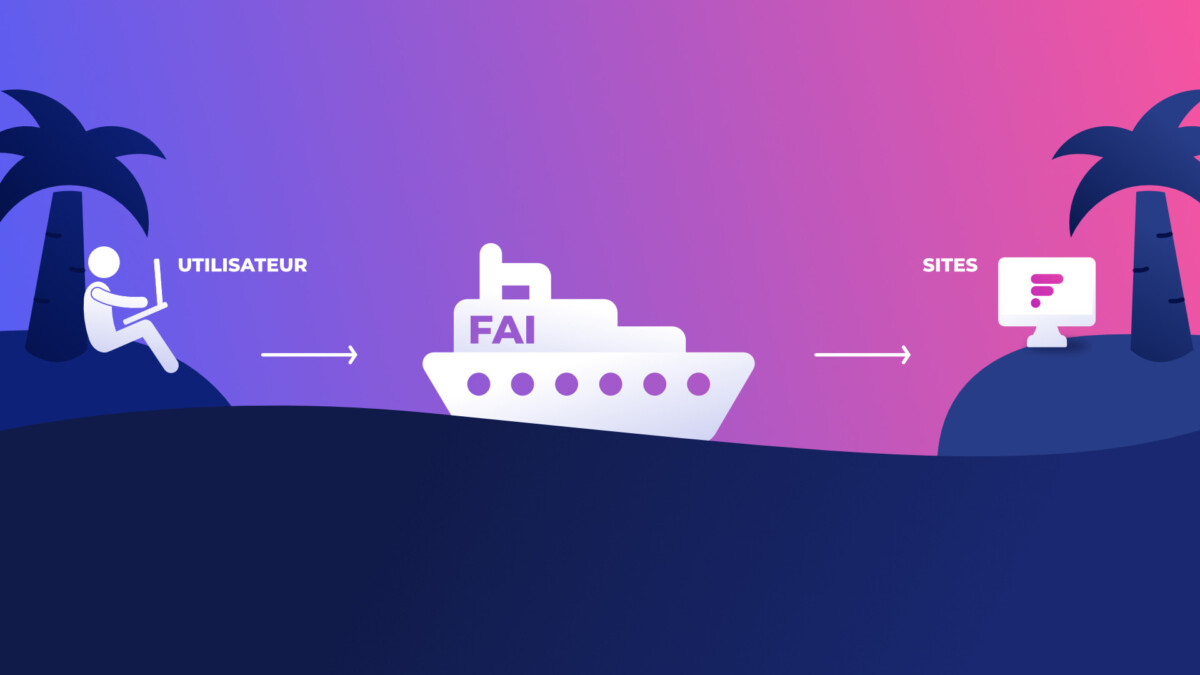
On the other hand, by using a VPN, you have a small pocket submarine, practical to carry everywhere with you, which allows you to navigate, under the surface, alone and without anyone knowing which island you are going to. (this is the VPN tunnel).
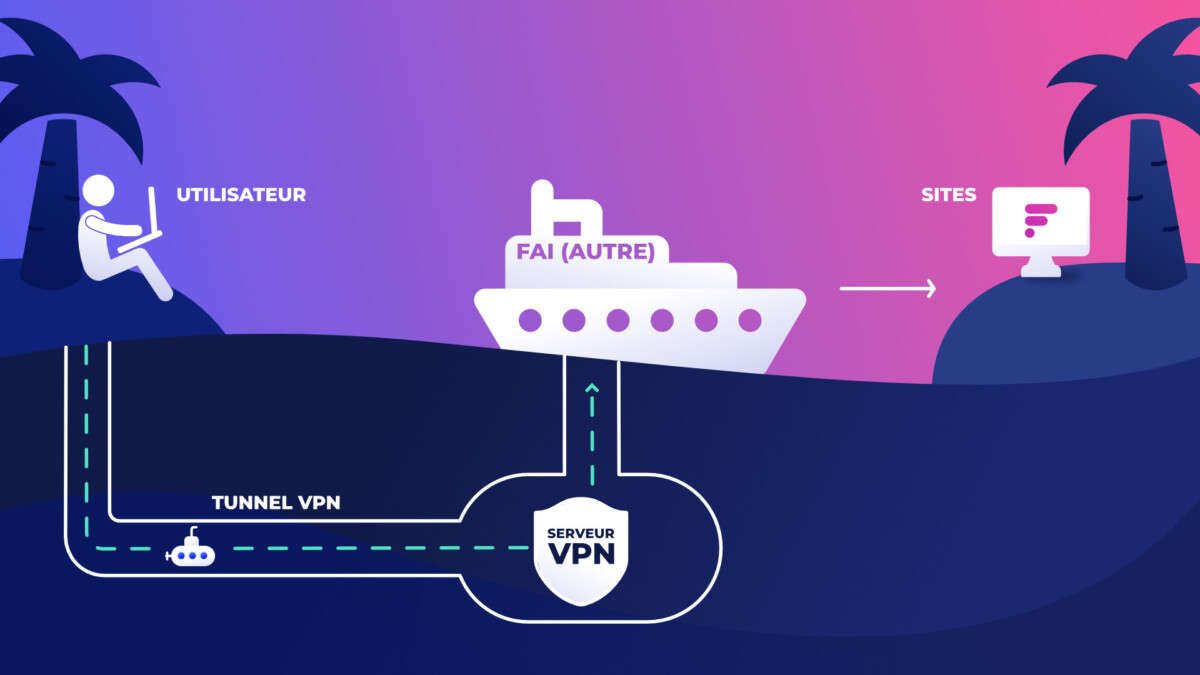
Note, however, that whatever happens, from your island, to get to your destination, you will have to go through an “underwater base” belonging to your VPN provider who will change the ferry company. This base is the VPN server.
In principle, this is what a consumer VPN offers. As part of a corporate VPN, you have to imagine that this underwater tunnel is accessible only to its employees and only to access its own island.
In fact, when you connect to the internet from your device, you activate your VPN access. This has the effect of creating, thanks to a VPN protocol (there are several), an encryption of your data and creating privileged access (tunneling) to a remote server, located in the country of your choice. Upon arrival on the server, your available information, such as the IP address of your device in particular, is made invisible to the eyes of the rest of the web, but also of your ISP.
How to take advantage of your VPN?
The VPN has the advantage of being compatible with almost all devices as long as they connect to the internet: console, television, smartphone, desktop or laptop computer…
Whether you’re installing a VPN on a fixed or mobile device, here are some commands you should understand and know to make sure you’re securing your connection properly.
- Choose the location of your VPN server according to your needs.
Changing the location of your connection is the basic element to configure and depends on your use. If you simply want to remain invisible on the web, you can choose a French server that will not allow you to be located or identified in your daily navigation.

If, on the other hand, you wish to prepare for your holidays, it may be interesting to locate yourself in the country of destination or in the continent of destination to carry out activity scouting and check the concordance of prices between your real location and your virtual location.
The same applies if you are traveling in a country which blocks access to certain sites or which practices censorship. Choose to locate yourself in a country where these blockages are non-existent.
- Activate it split-tunneling
Split tunneling allows, when you use a VPN, to create two connection channels. So some of your traffic can go through your ISP, and what you want to keep hidden from your provider goes through the VPN tunnel.
This allows you to make your connection more fluid. If you download an online game or an episode of your favorite series from a streaming site, split tunneling allows you to allocate your connection only to your most demanding activity, and let the VPN manage your ancillary activities, including you want to protect the data.

The kill switch is like the emergency button for your VPN access and it is strongly recommended to activate it.
Indeed, if the VPN connection is cut, the kill switch automatically disconnects you from the Internet so as to prevent your data, which until then has been encrypted, from being visible to anyone on the web.
Browse more serenely on the internet with a VPN
The VPN therefore responds to a few specific uses, but is a very useful tool as long as you understand the basics.
Understanding that the encryption path goes from your device, through a tunnel, to a server that encrypts your data is a solid foundation for understanding. Finally understand the usefulness of the available options such as the kill switchTHE split-tunneling or geolocation choices allow you to personalize your user experience.
And if the only question you still have is: which VPN to choose, say no more, the editorial staff has created a VPN comparator that you can consult here.
Our colleagues from Numerama are launching Watt Else, their newsletter dedicated to the mobility of the future. Sign up here to make sure you receive the next issue!
