Two-factor authentication adds a second layer of protection when you log in to a site. After entering a password, you must prove that it is you.
Double authentication, what is it? For several years now, passwords are no longer enough. Easy to divert (someone just needs to know your password to connect to your account), these vestiges of the web are bound to evolve, pending their disappearance announced with passkeys, which automatically identify a user on a page thanks to to a unique identifier stored on their device. In the meantime, double authentication (or 2FA) has emerged as the best alternative.
Double authentication adds a layer of security to your web accounts. The moment you insert your password, a site that offers two-factor authentication will perform a second check to prove your identity. This may be a code generated by an application, an SMS, a scan of your fingerprint on a special reader… Double authentication is in fact based on a known security logic: identifying oneself with the help of what you know (your password) and what you have (a code, a fingerprint, etc.). But there are plenty of ways to implement this tool, and not all are created equal.
How to implement double authentication?
Many sites offer double authentication. Google, Apple, Facebook, Instagram, Snapchat, Microsoft, PlayStation, Slack, Amazon… All offer this possibility to Internet users who want to take advantage of it. Some even force the hand of many Internet users, making it almost mandatory.
On the other hand, not all means of implementing 2FA (Two-factor authentication) are equal:
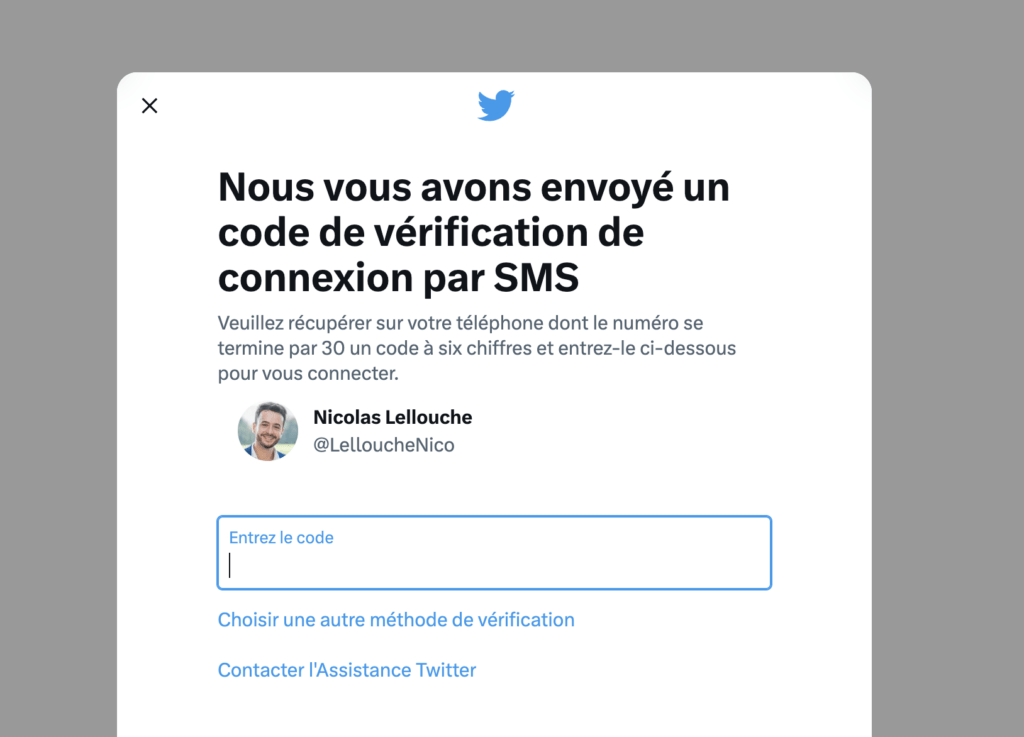
SMS
Authentication by SMS consists of communicating to the service that you are using your telephone number. Each time you enter your username and password, a code (usually 6 characters) is texted to you. This method is convenient because it doesn’t require any app or key, just a phone capable of receiving a text message.
Unfortunately, this is also one of the “easiest” methods to circumvent (well, easy, it still requires someone to use an antenna to intercept the content of an SMS or clone your SIM card … It is not within everyone’s reach). It also exposes you to the risk of phone number theft. It is for this reason that companies like Twitter have decided to remove the option.
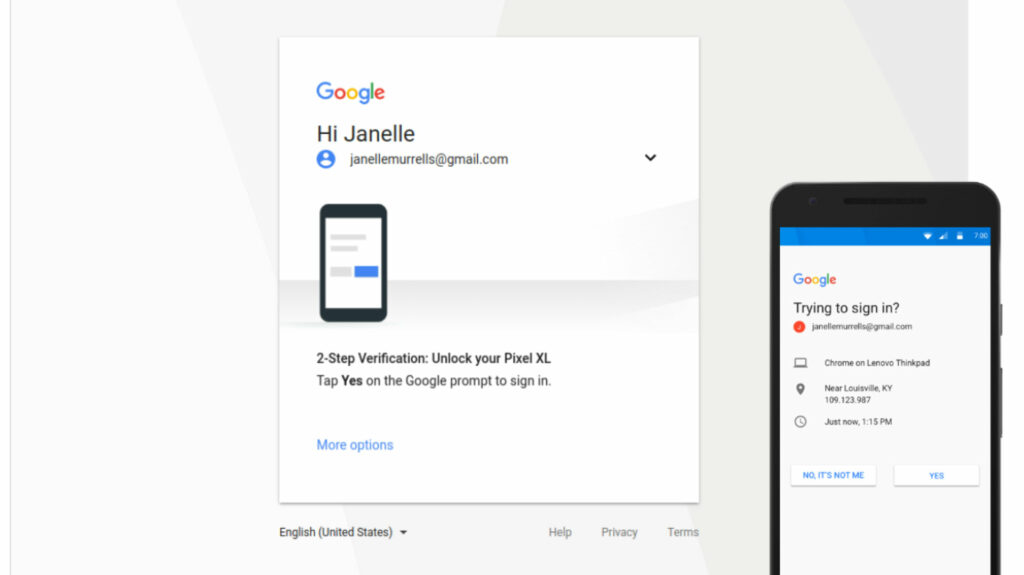
The login notification
Another popular option is the login guest. For it to work, you must already be connected to one of your devices, such as your smartphone (Google, iCloud or a bank account for example). Each time you try to connect to one of these services from another device (or want to make an online payment, for example), you will receive a notification on your smartphone. Without manual approval, impossible to connect.
In the case of a connection to a Google account, simply click on “Yes” on the pop-up that appears. The method is quite secure, because a hacker is unlikely to have a phone connected to your account. If you have more than one device connected to your account, however, the alert will appear everywhere. If a loved one tries to identify themselves on your behalf, they can potentially self-validate if a tablet of yours is lying around on the coffee table.
The authenticator app
An authenticator app is surely the best solution today. Simple to use, this software offers a high level of security. The idea is as follows: you download software like Google Authenticator Or Microsoft Authenticator. Then, from the site you are using (Twitter or Facebook for example), you choose the connection application option in the security settings. A QR Code appears on the screen, just scan it with the application.
Each time you connect to these sites, a verification code will be requested. You must then open your application and enter the 6-digit code that appears. These codes expire every minute, but renew automatically.
Rather secure, this method does have a drawback: you won’t be able to identify yourself on an unknown machine if you don’t have your phone handy. Otherwise, most sites offer “backup” codes for when you don’t have your phone on you (a text message, for example, which lowers security). Recently, there are also 2FA systems integrated into operating systems. An iPhone can for example store and generate its own codes, so that the user does not have to do anything.
The security key
The security key is probably the most secure method, but the most restrictive to set up double authentication. It consists of having a USB key that you insert into your smartphone or computer when you need to identify yourself. The best known of these keys is undoubtedly the Yubikey.
Security level, the solution is concrete, since it is based on a physical element, with a secure chip, to be inserted into your mobile or your computer. But you have to have it handy as soon as you identify yourself on an unknown machine. Not all web services are compatible with this solution, in addition. To be reserved for accounts hosting particularly sensitive information.

Conclusion
As we have seen, there are many ways to identify yourself with double authentication. All of them have qualities and shortcomings that must be taken into account when choosing the most suitable solution. Not all sites will necessarily offer all of these methods, so you may have to deal with these limitations as well.
But, whatever the method used, double authentication will always be preferable to the use of a simple password. You will find on Cyberwar tutorials to set it up on most major websites.
Subscribe to Numerama on Google News to not miss any news!
