Computer security is on the verge of a revolution with the arrival of passkeys. These access keys aim to replace passwords. On many criteria, they are superior to them.
Passkey? What is it exactly?
Passkey is an English term that can be translated as “access key” or “access code”. We can also hear about “identification key”. This is a new process for logging into an account, whether on a website or in an application. In short, it’s a kind of password, but of a completely new generation. In the very long term, the passkey aims precisely to replace the password.
Passkeys are not passwords. It is a mechanism that relies on pairs of cryptographic keys, a field called asymmetric cryptography. This involves two keys, one private (which is kept secret) and the other public (which is distributed). This is a common approach in computer security, for example, with end-to-end encryption of WhatsApp or Signal applications.
Why did the passkeys have to be created?
We have known for a long time that Internet users are not of impeccable discipline when it comes to creating a good new password. They are too short, too reused from one site to another, too common. In addition, sites can also make mistakes: store them in clear, or suffer a data leak. It is also a constant target of phishing attempts (phishing) in emails, SMS or online forms.
Security has relied on passwords for decades. Certainly, progress has been made. More and more platforms reject codes that are too weak. Strong authentication made it possible to add another layer, by validating a connection with a second action to be performed (entering a temporary code or validating an access request on a device). But, these are just additions to an existing system. The passkey leaves this frame.
” These key pairs profoundly improve security “, considers Apple, which has embarked on the adventure. Microsoft and Google too. Data leaks are not going to stop suddenly, and password hygiene is progressing moderately. It is therefore high time to kick in the anthill and build a whole new connection process.
What are the advantages of the passkey compared to the password?
Passkeys have several advantages over passwords:
- It is not necessary to memorize them;
These identification codes (for private keys) are stored exclusively on devices belonging to the same individual — basically, those logged into the same account, for example, from Google, Microsoft or Apple. These codes can be synced across devices. Terminals, in short, become sorts of password managers (passkeys, precisely). They are the ones who memorize everything.
- Passkeys are strong by default;
ID codes aren’t the kind to gather at toto123 or similar horrors. Each key is long and strong enough (to get an idea, they look like that kind of gibberish) that it can’t be guessed. They are also not reused or weak. These are unique codes. Exactly what should be done with his passwords, after all.

- Data leaks are not a problem (for passkeys);
The servers do not at any time host the private keys linked to the passkeys. They only have access to public keys. It is impossible to use one to find the other. Therefore, this data is less interesting for hackers. To have the private keys, it would be necessary to target the device of each Internet user. The task is far too difficult for large-scale action. What can always leak, however, is other personal data.
- Phishing is countered;
There are no more passwords with the passkeys, so there’s nothing to phish here. Access codes are intrinsically linked to the application or site for which they were created. Even if a fraudulent application or a booby-trapped site perfectly mimics the legitimate app or service, the system will see that there is a problem with the domain. He will note the absence of a public key (which is not in possession of the rigged site, but of the legitimate site).
How it works ?
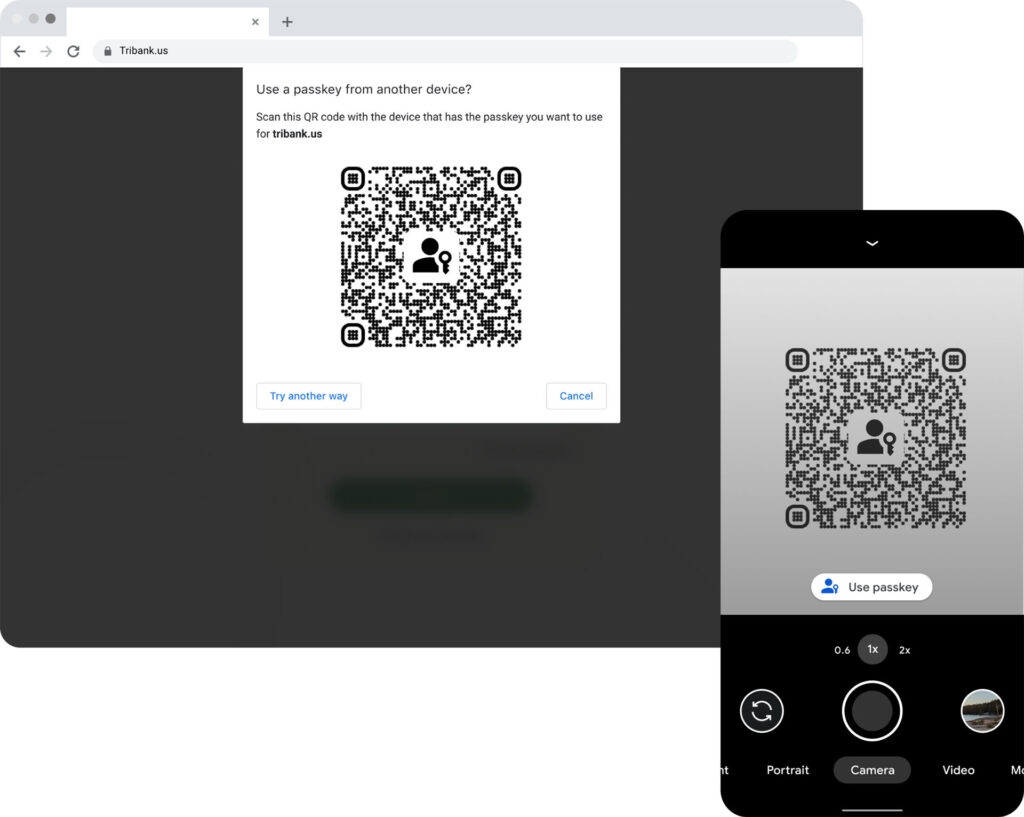
Basically, passkeys work like this: on the site or application of your choice, you ask to generate these access keys – if the device is of course supported. These keys work in pairs: one is public, which is kept by the site or app where you register, the other is private, and stored on your device (a computer or a smartphone).
As computer security professors Paul Haskell-Dowland and Steven Furnell explain in an article for The Conversation, “ the two keys are linked, but one cannot be used to obtain the other “. This is a crucial element: thus, if the website where your account is located is compromised, the public key alone will be useless. It will always miss the private key.
After the creation of your account, the connection to the site proceeds as follows: rather than typing a password, your device storing the private key serves as an intermediary to validate (and verify) your connection. For this, he can resort to biometric unlocking of the smartphone (fingerprint, face), a solution that is increasingly common on modern devices.
When the biometric stage has passed successfully, the device will then use the private key to prove your identity to the site, via a mathematical “challenge” complex to solve, detail the two teachers. ” At no time is your private key sent over the internet to the website “, they point out. Only the “response” to the challenge is transmitted to the website and verified via the public key.
Are the passkeys secure?
Can passkeys provide a full level of security? No. In this field, there is never an absolutely perfect solution. What matters, however, is whether passkeys are a real step up from an existing situation — like passwords, without sacrificing convenience. Overall, it’s much better.
” Unlike passwords, these keys are phishing resistant, they still offer a robust level of security and do not require the use of any shared secret. “, develops Apple in its pages of explanation. ” No shared secret is transmitted and the server does not need to protect the public key. » The risks are largely mitigated.
Of course, there are many scenarios that can outclass the protection conferred by passkeys, but this is the most common threat model for the average Internet user. This is what the two computer security professors point out: an attacker would have to compromise the biometric technology linked to the device, which requires a significant effort.
” To exploit a biometrics/private key combination, a criminal would have to first obtain your device and then successfully fake your face or fingerprint (or force your hand), which is unlikely for most users “, they detail. Fortunately, not everyone has spooks or mobsters on their heels.
The robustness of the passkeys is also much more interesting to deal with brute force attacks (consisting of testing all the combinations in order to find the right one) or social engineering (impersonating a technical service and obtaining communication password). Also, a leak on site A has no impact on the others, because each passkey is unique.
Internet users also do not need to remember it, which avoids the bad habit of writing it down anywhere and preventing it from being inadvertently given to an email or a fraudulent site. Very clearly, the benefit/risk balance is now very favorable to passkeys. It is potentially a game changer for all computer security on the Internet.
How to make passkeys a success?
The success of passkeys depends on several factors, starting with that of universality and compatibility: it will be imperative that devices, sites, applications, services can dialogue with each other in a fluid way, so that we can, for example, use an iPhone as an unlock mechanism for a Windows computer.
The passkeys being at a very preliminary stage of their existence, everything is not yet ready and functional. The good news is that Microsoft, Google and Apple are collaborating on these access keys so that everyone’s environments are not siled. It would be a disaster if a passkey generated via Android were not employable elsewhere.
Convenience of use is also key, because not everyone is a nerd sysadmin biclassified hacker and master dev. Many do not want to get their hands dirty and go through a first preliminary configuration phase that lasts three hours. Nor to rub shoulders with an incomprehensible interface. For it to work, it will have to be simple and sober.
If biometric technology will certainly be called upon to be the central lever for using passkeys, alternative solutions will also have to be considered. For people who refuse to use it, but also in the case where devices are used that are not equipped with adequate sensors. This could be a PIN code or a security key.
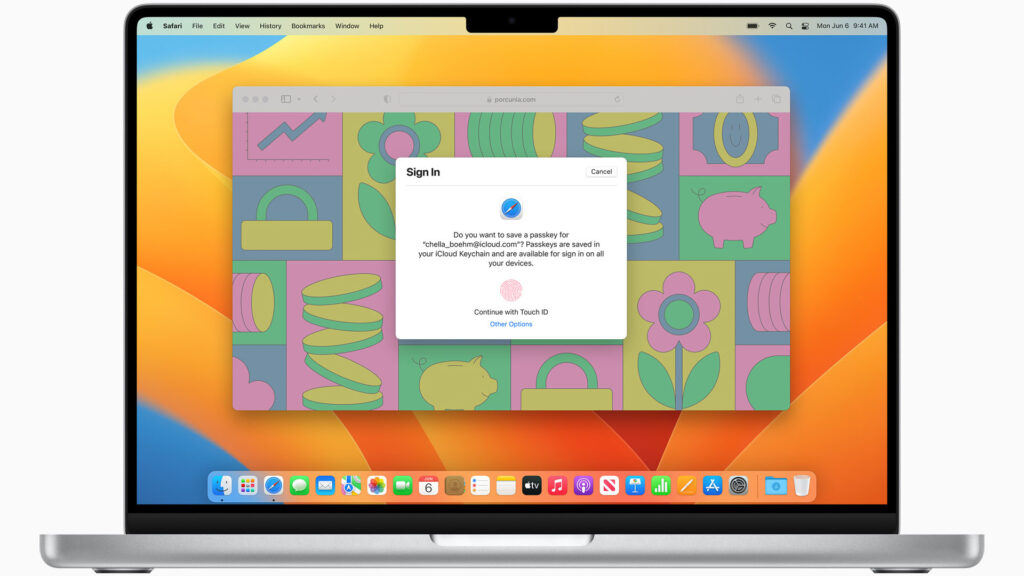
Other issues will also have to be addressed: how to revoke a passkey in favor of a new code? How to synchronize these keys between legitimate devices of the same person? Companies that have embarked on this system are already addressing some of these questions. For example, Apple provides synchronization between devices via iCloud Keychain.
What about passwords? What will their future be?
While passkeys may be the future of computer security, it’s a future that won’t happen any time soon. We can assume this by observing the speed with which double authentication is spreading among the general public: not everyone uses it, whereas solutions have been available to everyone for years on a number of sites and services.
The two solutions should also coexist for a long time. Password managers therefore need not worry in the immediate future, even if the main ones began last year to adapt to also be passkey managers. This is the case of Dashlane, 1Password, LastPass and Bitwarden, in particular.
The long tail of passkey adoption promises to be devilishly extended, and in doing so, passwords aren’t going to get any closer to the left. Once the wave of early adopters has passed, it will be necessary to engage the switch of the general public, companies, public institutions and everything that uses a password. Nothing says that everyone will take the plunge.
Subscribe to Numerama on Google News to not miss any news!
