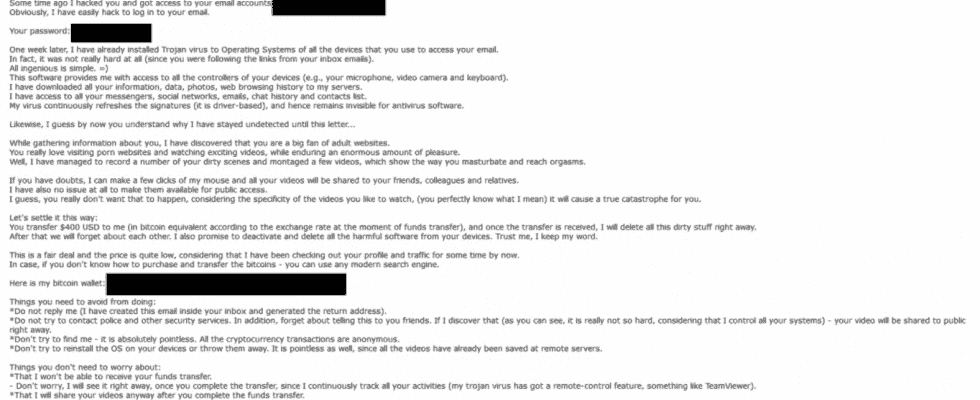
A phishing email with the subject “ALARM – I’m hacked you and stolen you information and photo” is in circulation. In this, the sender blackmails you.
You are being blackmailed in this English-language phishing email. (Source: consumer center)
- Cybercriminals demand bitcoins from you in a phishing email.
- They blackmail you with supposed videos on which you visit pornographic sites.
- Do not respond to the demand, these are empty threats.
Criminals try to blackmail you with a well-known phishing scam. You can recognize the attempted fraud by an English-language message with the subject “ALARM – I’m hacked you and stolen you information and photo”. In this, cybercriminals claim to have videos of you on which you look at pornographic content. To prevent the material from becoming public, the criminals demand $400 in bitcoins from you.
In the email, the blackmailers explain to you at length how they spied on you. A Trojan has allegedly been smuggled into your system, which the criminals used to gain access to your social media and e-mail accounts. Your personal data and browser history are also said to be in the possession of the attackers.
Upon receiving the ransom, the criminals promise to delete the blackmail material and the Trojan and leave you in peace in the future. If you refuse or call in the police, they would immediately publish the videos of you online.
According to the consumer advice center, passwords that are mentioned as proof in the mail can match yours. However, the content is fictitious. Don’t let the empty threat intimidate you. The blackmailers have no means of leverage. You can simply delete the email or report it to the police.
Simple signs: This is how you recognize every phishing email
A first indication that you have received a phishing email: The email will ask you to confirm personal data or to enter it on a website. This Under no circumstances should you comply with the request. In addition, criminals often use the official logos of the companies they are copying in their emails, but not official sender addresses.
If you find the sender suspicious, you should read the email twice. You will often find spelling mistakes or inconsistencies in German grammar. The attackers usually do not write their emails themselves, but instead use automatically generated messages or translate known emails with a translation program. But why all the effort?
What do criminals achieve with phishing attacks?
Phishing is used on the Internet to collect real user data. Money can be made with these if e-mail addresses, names and other information are sold for advertising purposes or passed on in criminal forums. With the data obtained, cyber criminals can also address future phishing attacks in a more targeted manner, making their attacks more effective.
Did you receive a suspicious email?
Forward them to [email protected]
or follow us on:
Phishing Checklist
- ✔
Spelling mistake? - ✔
Sensitive data requested? - ✔
Official logos? - ✔
Unknown sender?
Attachments and links contained in malicious e-mails also often inject malware or viruses onto your computer. In addition, you should not simply ignore suspicious emails. Forward them to the above email address and help us report future phishing attacks.
More fraud alerts on netzwelt – stay one step ahead of cybercriminals
But phishing emails are not the only danger lurking on the internet. In addition to fraud attempts, there are all kinds of viruses, Trojans and malware that can infect your computer. Unfortunately, data scandals are also part of everyday digital life. You can see the five most recent articles on the subject of “Scam Alerts” below:
Do you want to stay informed about the latest fraud reports, Subscribe to netzwelt on Twitter, Facebook and Instagram. You can also find all articles on the subject on the next page.
Don’t miss anything with the NETWORK-Newsletter
Every Friday: The most informative and entertaining summary from the world of technology!