Her name ? Vcurms, and it is part of the family of malware. His target? The most common browsers and applications used on Windows.
The Internet has almost as many users as pirates. And unfortunately it is one of their new malware which has expanded this dark family. Discovered by researchers at Fortinet’s FortiGuard Labs, this worm, called Vcurms, is a new threat targeting the most popular browsers and applications to steal data.
To spread this computer worm, hackers use email as a command center and cloud services such as AWS and GitHub to store the malware which poses even more of a high risk for systems equipped with Java, allowing full control to the attackers.
Hackers, who doubt nothing, use Proton Mail, a VPN and its well-known secure messaging service to escape detection. FortiGuard Labs recommends security updates and increased vigilance with email.
Vcurms threat propagation circuit
Vcurms is notable for its ingenious distribution methods and ability to evade detection.
The attackers’ modus operandi involves tricking users into downloading a malicious Java downloader, which serves as a vector for spreading Vcurms and STRRAT, a fearsome Trojan. These attacks are often disguised in sophisticated, seemingly legitimate emails that trick recipients into verifying payment information and downloading harmful files hosted on popular platforms like AWS.
Once downloaded, the malware exhibits classic phishing characteristics, using spoofed names and obfuscated character strings to disguise its harmful nature. It also deploys advanced obfuscation techniques to evade detection and analysis, including the use of a class named “DownloadAndExecuteJarFiles.class” to facilitate downloading and executing additional JAR files.
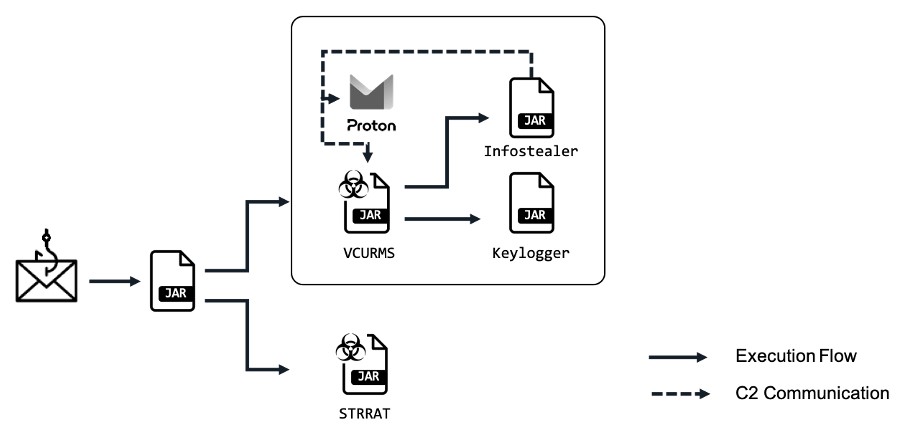
The Vcurms Remote Access Trojan (RAT) communicates with its command and control center via email, demonstrating an alarming level of sophistication. It establishes persistence by replicating itself within the Startup folder and uses various techniques to identify and monitor victims, including keylogging and password recovery features.
Objective: target the most popular browsers and applications
In addition to its innovative distribution method, Vcurms stands out for its ability to effectively target the most used browsers and applications. It primarily steals sensitive information from popular browsers like Chrome, Brave, Edge, Vivaldi, Opera, Opera GX, Firefox, as well as apps like Discord and Steam.
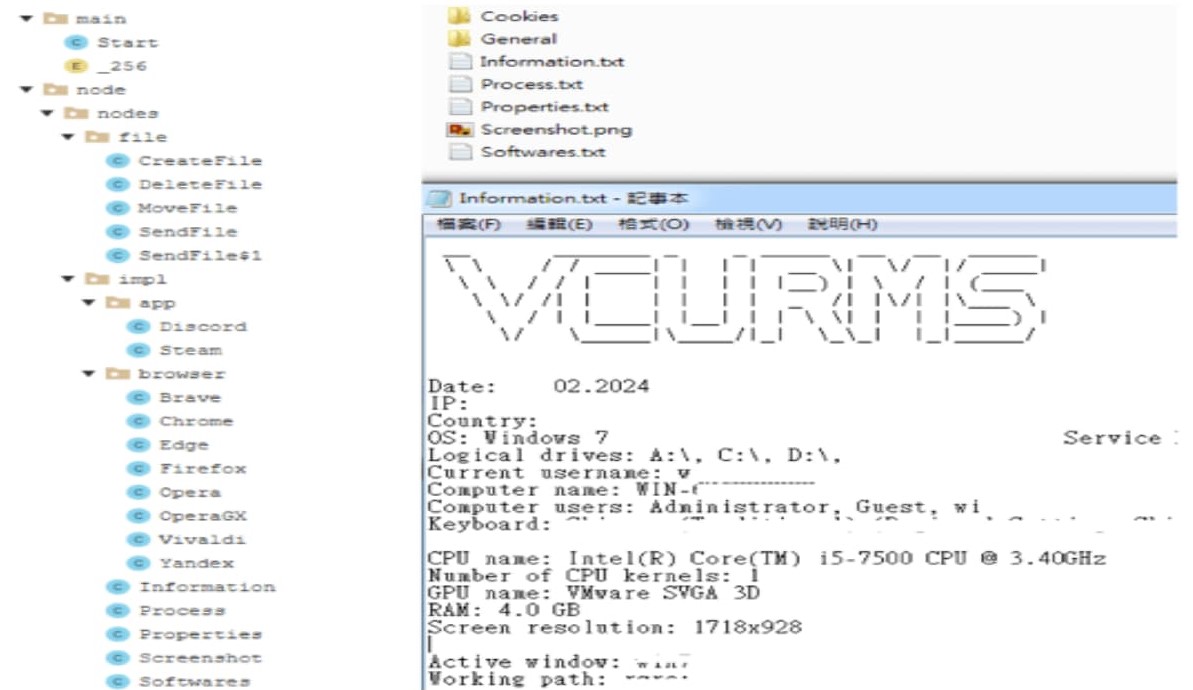

Despite the challenges posed by these sophisticated attacks, cybersecurity researchers continue to develop methods to deobfuscate (decrypt) Java code and understand the inner workings of Vcurms.
In the meantime, prevention remains, as always, the best defense against these threats.
Jason Soroko, senior vice president of product at Sectigo, warns of the danger of outdated authentication methods. “ Malware authors are taking advantage of cloud computing. RAT malware typically harvests whatever it can, and the new remote access trojans VCURMS and STRRAT appear to have one or more keyloggers », he warns, before specifying the importance of using stronger authentication methods than a simple login by username and password.
Source : Hackread, Fortinet


1