Data is cool, Bitcoin and cryptos are better – The first edition from our mini saga exposed the massive flaws of “web2”, a critical subject that is too little discussed publicly. However, there is an urgent need to deal with it as best as possible in order to try to avoid new breaches. The war on the net is global and uninterrupted. The Internet contains treasures of information for those who know how to extract and exploit them. Some GAFAMs even have a business model that relies heavily on customer data. But impossible for us to throw stones at them, since we have fully read and approved the general conditions of use of these platforms.
In this second episode devoted to cyber insecurity, we will focus on the crypto sector. The “web3” almost “logically” inherits certain weaknesses from its ancestor, which weakens it enormously. The crypto ecosystem aims, among other things, to disrupt traditional financial services and attract more and more liquidity to its protocols. Which earned him a target in the back.
the sector is still young and immature, despite an already heavy financial responsibility. The concepts and tools (even the wallets) crypto are poorly understood and still too complex for some investors, who in fact become potential targets. Even if the education around these subjects progresses visibly, the scams persist and the pirates redouble their ingenuity. Weak computer code, human errors and evil geniuses: an overview of the dangers of web3.
>> Sign up on Binance and get 50% off entry to Binance Blockchain Week with the code Paris50JournalDuCoin (commercial link) <<
Cryptos, DeFi, NFT: everything goes
Let us sweep away the famous ” we are here for the tech “. The primary interest of each new entrant is financial. It is also that of the sharks that prowl around the nascent crypto galaxy. Whether they act in small groups or real elite units, whether they are supported by patrons of crime or not, these dishonest actors have understood that the crypto vein could pay off big.
The summer of 2022 was particularly hot in terms of hacks and millions of dollars stolen. From bridge Nomad ($190 million) at siphoning of 10,400 wallets Solana passing through the misappropriation of $500,000 of NFT on Premint, the summer period is not synonymous with holidays for pirates. They seem more and more determined and organized.
It must be said that the cake is enough to make your mouth water and that it does not always seem to be adequately protected. The reference site DeFi Llama currently counts, just over $60 billion locked in various protocols with prompts (incentives) economical. A total that was more than three times higher ($192.8 billion) at the top of the last bull cycle at the end of 2021.
The favorite targets of hackers are DeFi protocols, NFTs and bridges, which Vitalik Buterin has himself identified as a weak link in the network to date, a potential attack vector. Although more so potential than that: Solana and its users have indeed had great scares, on several occasions.
The bridge Wormhole between Ethereum and Solana has thus seen 120,000 ETH evaporated ($326 million at the time) of its smart contract last February. This gaping hole in the crates would have been far-reaching consequences for DeFi and NFT on Solana without the intervention of Jump Crypto, the company that develops Wormhole. The company potted without flinching because it ” believes in multichain future and it is essential infrastructure […]that’s why we reinjected 120,000 ETH to compensate the community according to details obtained by Blockworks.
For its part, Bitcoin is not targeted by this type of hack. Although it can be criticized for it, the fact that Bitcoin serves almost exclusively as a safe haven (digital gold) or an exchange currency, gives it its resilience. The entire Dapps (decentralized applications) market is driven by Ethereum and altcoins.
BTC is still the subject of many scams, which mainly target beginners and gullible people. No one will ever double the bitcoins you send them, let alone an anonymous stranger.
On the other hand, hackers mainly convert their loot into BTC after their robberies.
Infrastructure in the dock – The royal road for hackers
Like “web2”the “web3” is in part based on open source code. Although this serves a philosophy stemming from the internet culturethis also serves as malicious individuals. As we mentioned in the first episode, thousands of code libraries themselves used by thousands of companies, are infected with viruses.
Crypto protocols are also exposed to this threat, whether directly or indirectly. The smart contracts are the cornerstone of the new internet economy. They make programmable money and allow new online uses, more or less decentralized. For better and sometimes for worse.
Regularly, clever minds detect weaknesses in a part of a smart contract’s code and take advantage of it. This is the recent case of Reaper Farma service of Challenge based on the Fantom blockchain. Hence the importance of a reliable and serious audit by independent bodies. You also need to have basic digital hygiene reflexes.
Although honest, some developers and project managers are simply not competent or aware of the dangers. To the point ofhost private keys of a crypto wallet service on a shared file, hosted on centralized servers… We believe we are dreaming. There it is clearly not a problem of development or computer code, it is a purely human error.
The collaborative internet also shares its bad sides
On the computer side, the code of a protocol must be irreproachable, but even if its “crypto” part is so… it can inject (without knowing it) corrupted open source code. As cybersecurity expert Anis Haboubi points out.
And that’s where the shoe pinches: the contagion seems as massive as it is discreet, and affects “web2” as well as “web3”.
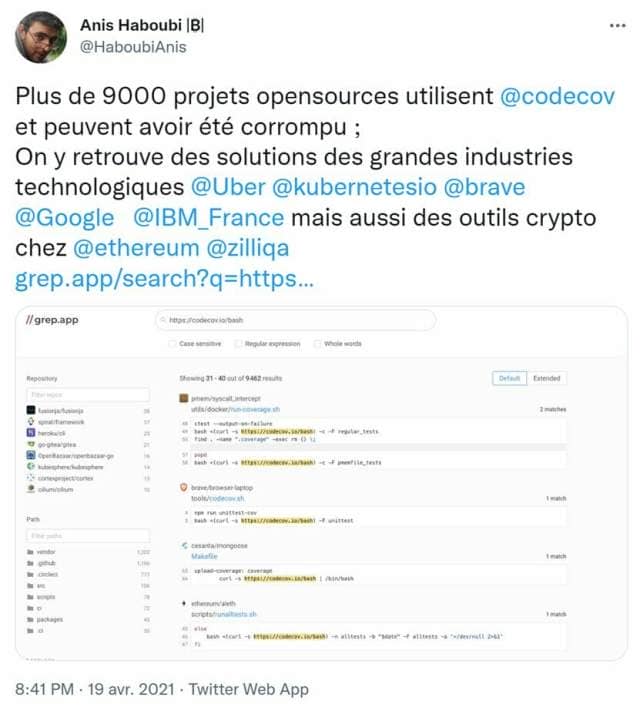
This tweet dating from April 2021 alerted to the corruption of more than 9,000 open source projects through Code Coverage services. Code Coverage is an analysis tool for scanning computer code and identifying the lines of code executed during a test.
This solution offers considerable time savings for developers. So practical even, that among its customers we find products:
- Ali Baba
- Microsoft
- Mozilla Mobile
- Zalando
- Spotify
- Brave
- Ethereum
- Ziliqah
This (non-exhaustive) list shows the extent to which all companies are targeted, even GAFAM members. In view of the annual turnover of some of these companies one could imagine an irreproachable security, but this is not the case. So imagine the threat to crypto startups with less solid backbones. Especially since many projects use Code Coverage solutions, the flaws of which are no longer to be demonstrated…
>> Sign up on Binance and get 50% off entry to Binance Blockchain Week with the code Paris50JournalDuCoin (commercial link) <<
Crypto scams and hacks: increasingly advanced techniques
The persistence of attacks and their degree of sophistication should alert us on several levels:
- The determination hackers to harm these companies and their customers (and more)
- the technological and financial support (or even more) that hackers benefit from
Regularly, computer security experts detect new bridges, new ways to break into computer systems. So-called “supply chain” attacks are commonplace. It must be said that the vein is too juicy and that the interconnection of services and products via hacked code libraries offers an unprecedented attack surface to pirates.
The attacks we report here are very well put together and some elements clearly point to large-scale cyber attack programs. They also attack large targets, investment funds, emblematic personalities or some official accounts are targeted. In the screenshot below, the hackers were trying to impersonate respected community member Sisyphus.
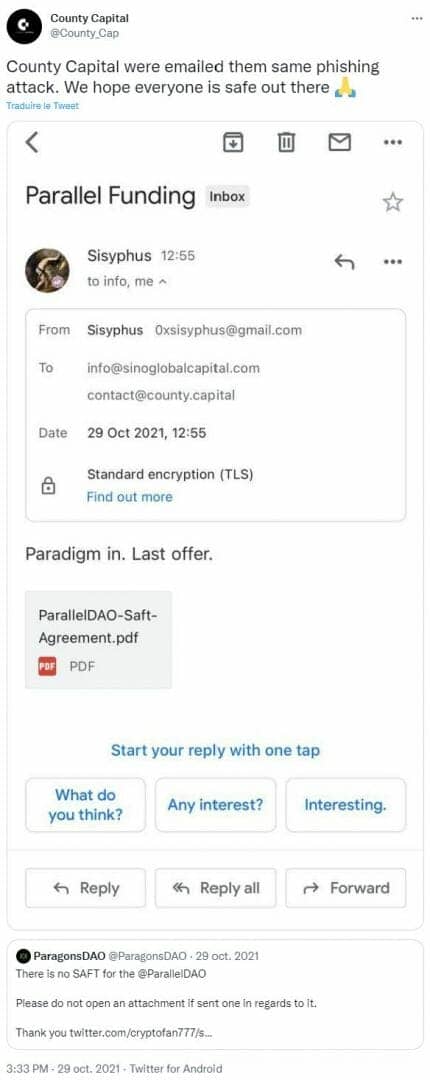
Earlier this summer, the very famous collection of NFT Bored Ape Yacht Club saw his Discord server hacked (140 ETH diverted). The hackers took the opportunity to post links to phishing sites, recovering private keys and sensitive information from Internet users who clicked on the link.
All means are good
Among the latest trends to find an entry point to a network that is a priori secure, recruitment announcements. Google unveiled this technique already last year, after several of its researchers were targeted, and even compromised.
Hackers’ technique is to create (or usurp) “reliable” and “credible” profiles. Once control is gained over such an account, hackers contact people in critical positions in the organization chart of a company, in particular in IT security departments, and offer them fake interviews for a fake recruitment. Or to perform an update and to do this you must download a attachment or one malware. This scheme has been used many times against crypto protocols and their networks.
Ultimately, no attractive job at stake, but a siphoning or even total access to the data present on the candidate’s machine. The technique is mainly used on Twitter and Linkedin.
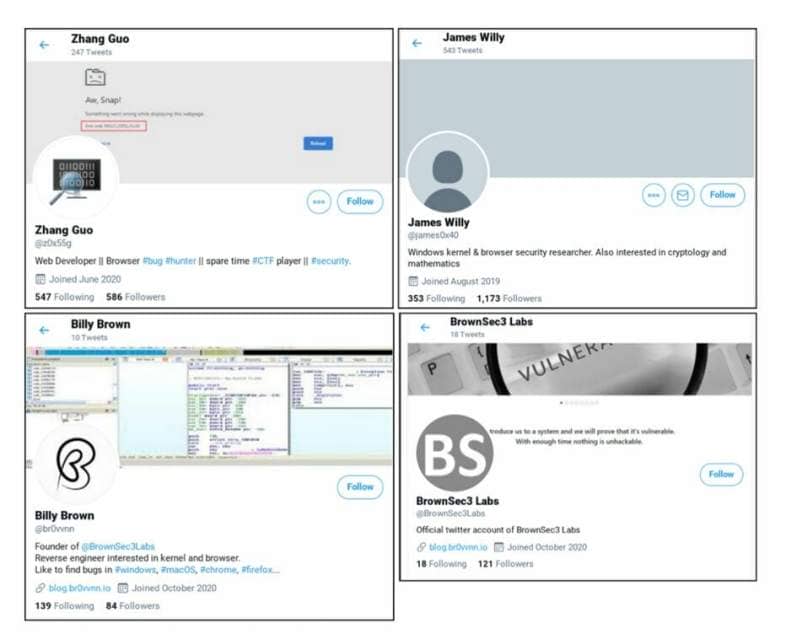
Once again, the attacks seem calibrated and target very specific personalities, who possess sensitive data. It is part of stigmata which suggest that these are not not “Sunday hackers” who work there. By linking together the major attacks of the past few years, computer security researchers seem to understand the logic behind it, and all that it entails. A logic not only financial, but Politics.
Italy’s foreign minister said a few days ago that attacks targeting Western European companies had increased since the invasion of Ukraine (Bloomberg).
The term cyber warfare is clearly not overused and if it was, it will be less and less so. The objective of these offensives has taken on more and more meaning in recent years. A more global pattern is emerging as researchers update ” backdoors ” and others ” zero day exploits “. But for a war, you need an army and an army does not go to the front with toothpicks. Who Arms Crypto Hackers?
Cyber-insecurity and crypto hacks: who benefits from the crime? Third and last part of this mini-series, to be published next week on the Journal du Coin.
Don’t miss the back-to-school event thanks to the JDC! Register on Binance and get 50% off entry to Binance Blockchain Week with code Paris50JournalDuCoin (commercial link).
