The U.S. Cybersecurity and Infrastructure Security Agency (CISA) released its own Log4J flaw detection tool this week, along with many other cybersecurity companies and researchers.
Open source, this tool is a derivative of scanners created by other members of the open source community. It is designed to help organizations identify potentially vulnerable web services affected by Log4j vulnerabilities.
The American agency explains that it relied on an analysis tool created by the security company FullHunt to detect these same security vulnerabilities, and received the help of other researchers such as Philipp Klaus and Moritz Bechler.
Identify security vulnerabilities affecting Log4j
The repository provides an analysis solution to find security vulnerabilities CVE-2021-44228 and CVE-2021-45046. CISA clarifies that the solution supports DNS callback for vulnerability discovery and validation, while providing fuzzing for HTTP POST data parameters, fuzzing for JSON data parameters, and list support. ‘URL.
It also offers WAF bypass payloads and fuzzing over 60 HTTP request headers.
Crowdstrike has also released its own free Log4J scanner, called “CrowdStrike Archive Scan Tool”, or “CAST”.
Testing the scanners
Yotam Perkal, Vulnerability Research Manager at Rezilion, has tested some of the Log4J vulnerability-focused detection tools. He finds that many of them are unable to find all instances of the vulnerability.
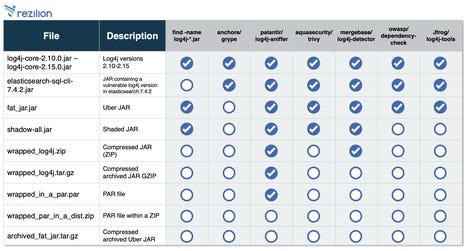
Picture: Rezilion.
“The biggest challenge is to detect Log4Shell in packaged software in a production environment: Java files (like Log4j) can be nested at multiple levels within other files, which means that a cursory search of the file will not find it. not ”, explains the researcher. “In addition, they can be packaged in many different formats, which creates a real challenge to find them inside other Java packages. “
Rezilion tested the nine most common scanners used by developers and IT teams on a packaged Java file dataset where Log4j was nested and packaged in different formats.
The limits of detection tools
Yotam Perkal specifies that while some scanners do better than others, none is able to detect all formats. According to him, this research illustrates “the limits of static analysis in the detection of Log4j instances”.
“It also reminds us that detection capabilities depend on your detection method. Scanners have blind spots, ”he adds.
“Cyber security managers can’t blindly assume that various open source or even commercial tools will be able to detect all borderline cases – and in the case of Log4j, there are a lot of borderline instances in many places. “
Source: ZDNet.com
