Made public for a little over a week, the Log4Shell flaw
gives rise to cascading discoveries of breaches and vulnerabilities. For example, researchers have discovered that renaming a iPhone
could allow an unprotected link to Apple servers.
Discovered on a Java library used by many industry players, including Apple and Tesla, the Log4shell flaw makes it possible in particular to run malicious code, without authentication, to access servers. This zero-day flaw is described as ” extremely serious By security researchers who first identified it in November.
Apple and Tesla vulnerable, at least theoretically
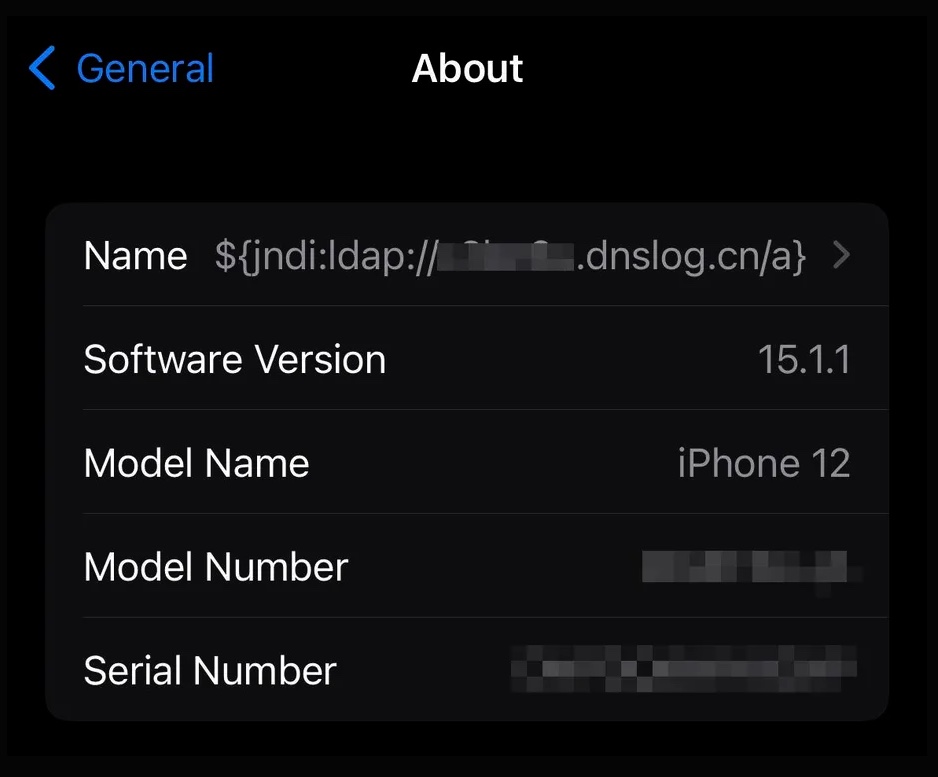
Further proof of his insidious nature, we recently learned by The verge that replacing the name of an iPhone with a code was enough to get a ping (and therefore a point of contact) from Apple’s servers. This flaw is also observed at Tesla.
The researchers behind this other discovery simply replaced the name of the device with a specific string of characters. The latter is created to send the servers to a test URL. This makes it possible to simulate their behavior in the hypothesis that they would actually be confronted with an attack by this means.
And the results are worrying: this name change did indeed lead Apple’s servers to visit the URL previously chosen by the researchers. In the context of an attack, the consequences of this vulnerability could be serious and lead to the loading of remote resources, such as malicious code. Needless to say, this shouldn’t normally be possible with a simple name change.
A loophole filled … but which should be rife for a while
That said, The verge specifies that if this demonstration once again shows the potential dangerousness of the Log4shell flaw and its ramifications, it remains unclear whether cybercriminals could really take advantage of this name change to harm Apple or Tesla’s servers.
” In theory, an attacker could host malicious code at the target URL in order to infect vulnerable servers, but a well-maintained network could prevent such an attack. “, Explains the American media in particular.
Note also that an update and fixes have already been developed and deployed to plug the Log4shell flaw. As is often the case with this type of zero-day vulnerabilities, it will nevertheless take time for all vulnerable machines and servers to be patched.

After having alerted to the issues of personal data protection, then drawn up a list of concrete actions to be taken on your computer and your smartphone in two files (accessible at the end of this article), the time has come for deepening.
Read more
Source: The verge

7