Taking advantage of Internet users’ interest in space and the images captured by the James Webb telescope, hackers launched a phishing campaign based on the integration of malware into a JPG.
Every time NASA publishes a snapshot of the James Webb Space Telescope, it is the effervescence. Many Internet users flock to the images to observe new points of view on the distant universe through unique photos. A craze that has not escaped hackers, who exploit these images to deceive users and infect their devices.
Securonix cybersecurity experts have investigated this new kind of campaign, called GO#WEBBFUSCATOR. The malware thus distributed is written in the Golang programming language, which has the advantage of being supported by the main desktop supports: Windows, Linux and macOS.
James Webb telescope images as a phishing attempt
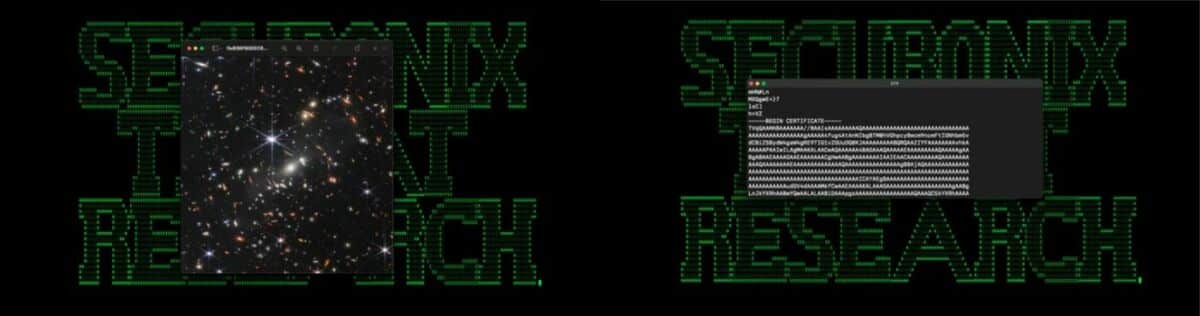
To trick victims, hackers use the well-known technique of phishing. An email is received by the target, who is encouraged to open the attachment to discover an image captured by the James Webb Telescope. This is a photo released by NASA last July, which shows SMACS 0723, a cluster of galaxies located more than four billion light-years from Earth. This composite image has been named Webb’s first deep field and is an event for astronomy enthusiasts since it is the first taken and made public by the James Webb telescope.
The image sent by hackers is hidden in a Word file by the name of Geos-Rates.docx, which contains a malicious macro that runs automatically when the file is opened. If you have macros disabled in your Office suite, then you are safe. If this is not the case, the code will allow the downloading of a JPG image, which itself hides an executable .exe file, which will then launch.
In an image viewer, the JPG file does show SMACS 0723. Opening it with a text editor reveals the presence of Base64-encoded content, which turns into a malicious 64-bit executable file.
Source: Securonix