One of these data blockers is fake and could hack your computer if you plug it into the data port! Adrian Kingsley-Hughes/ZDNET
Data blockers, also known as USB condoms, are one of those cheap security tools that I recommend keeping in a pocket or bag for anyone who might use a random charger. Along with a good VPN, antivirus software, and an encrypted USB drive, this is one of the modern security tools I consider essential.
Okay, first of all, what is a data blocker? This is a small dongle that adds a layer of protection between your device and the electrical charging socket you plug it into. It allows charging but blocks all data communication by physically cutting the USB data lines, which creates a “gap” between the USB port and your smartphone, laptop, or other device you’re charging.
Why is this important? USB is not only a charging protocol, it also allows data to flow in both directions, and while most of the time this data flow is safe, it is possible to create a malicious charging port like who will steal your data.
I’m a big fan of the data blockers sold by PortaPow. These blockers are an inexpensive and very simple solution to the problem of using unreliable USB charging devices.
The other day a reader told me he was at an airport where someone was “giving away USB data blockers for free,” and he wondered if I found that a bit strange.
Well, it is, because quite honestly, I wouldn’t trust a USB device randomly handed out to me like that. It could be anything and, after all, there are malicious data blockers in the wild.
Take a look at the image above and see if you can spot the fake data blocker. Do you see it ? No ? It’s This one.

Fake data clocker among a bunch of real ones. Adrian Kingsley-Hughes/ZDNET
This is a fake data blocker made by a company called O.MG called the UnBlocker. Although there are many homemade methods for making a fake malicious data blocker, this is a very high quality commercial blocker that is difficult to distinguish from a real data blocker. Unless you know what to look for!

The O.MG UnBlocker. Adrian Kingsley-Hughes/ZDNET
Outwardly, it looks like an ordinary data blocker, but inside it is equipped with hardware that can be used to install malicious payloads on devices, and it is even possible to connect to it remotely using Wi-Fi.
Here, I’m using a special scheduler to initialize the UnBlocker and prepare it to do… well, anything.
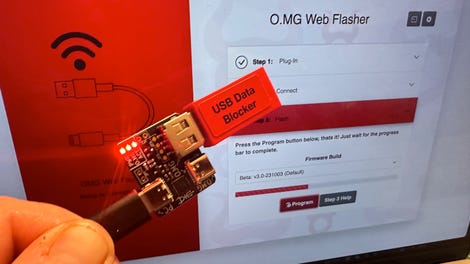
Initialization of the O.MG UnBlocker. Adrian Kingsley-Hughes/ZDNET
OK, now how to spot a fake data blocker?
Look closely at the PortaPow data blocker’s USB jack and notice that it only has two connectors and that the two middle pins (the ones used to transmit data) are missing. There’s even a cutout on the top of the USB jack and the words NO DATA are printed clearly on the connector.

The two center pins of the USB jack are missing, meaning this jack cannot carry data. Adrian Kingsley-Hughes/ZDNET
For those who want to ensure that their data blocker has not been tampered with, PortaPow also makes transparent data blockers, please note.

PortaPow also makes a transparent USB data blocker. Adrian Kingsley-Hughes/ZDNET
Compare this to the UnBlocker, which has all four pins! This is an immediate red flag.

The UnBlocker is equipped with all four USB pins, which means it can carry data. Adrian Kingsley-Hughes/ZDNET
Another way to spot a malicious data blocker (or cable or dongle) is to use a malicious cable detector. Plug one end of the malicious cable detector into a USB socket (not into a device like a PC!), and the other end into the device of concern (e.g. a USB key): if the logo lights up bright red, something suspicious is happening.

The Malware Detector detects that the UnBlocker is an active device. Adrian Kingsley-Hughes/ZDNET
At $150 each (because that’s how much they sell for), I don’t think anyone has distributed UnBlockers at an airport (unless the hackers are targeting someone very important), but I I wouldn’t plug such a device into one of my devices.
I recommend purchasing your own data blockers and possibly personalizing them with stickers or nail polish or engraving your name on them so they can’t be swapped or altered, and making them part of your pencil case of travel.
Prevention is better than cure !
Source: “ZDNet.com”
