More than a year ago, in parallel with successive deployments of The Merge and hard fork Shanghai, Ethereum has chosen to entrust the scalability issue to second-layer solutions. Thus, this paradigm shift tends to shift real activity to layers 2 and to use Ethereum as a settlement layer. (settlement) and data availability.
Layer 2 (L2): the crux of the matter on Ethereum
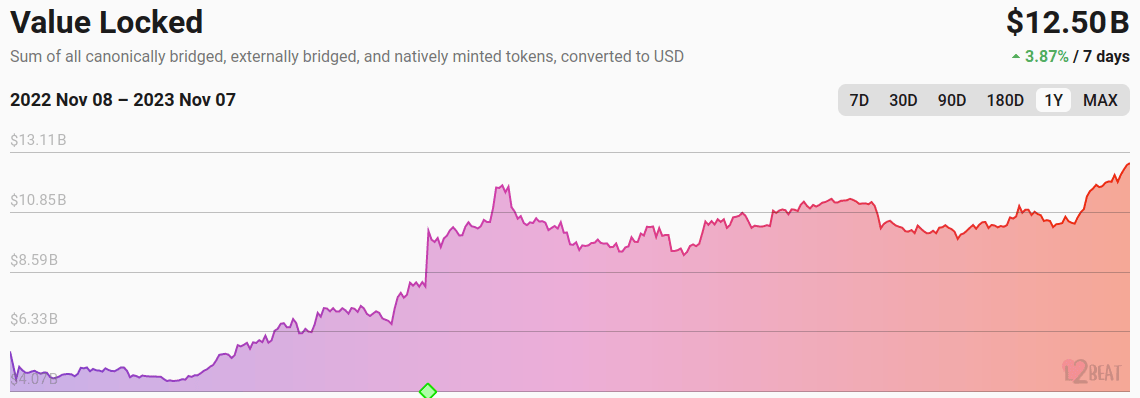
Since the start of the year, these solutions have been on the rise. So, in turn Optimism, Arbitrum or Base were the focus of attention. So much so that in the space of a year, the TVL of layers 2 of Ethereum went from 5 to 12 billion dollars.
However, not all of these solutions take the same approach. Indeed, there are a variety of different architectures for L2s, each adapting the compromise between security, scalability and cost in its own way.
In addition, not all applications hosted on these layers 2 have the same needs with regard to the previously mentioned trilemma. For example, an application of decentralized finance will place particular importance on security, even if this comes at the expense of scalability and cost. On the other hand, an application of social network will place more emphasis on scalability and cost for its users.
As many specificities as Vitalik Buterin recently discussed and analyzed in an article published on his personal blog.
Security vs scalability
To begin with, Vitalik Buterin explores the relationship between security and scalability to define a layer 2. It asks the question:
“If you have an asset issued on L1, then deposited on L2, and transferred to you, what level of assurance do you have that you will be able to bring the asset back to L1? »
Vitalik Buterin
In other words, the security of your asset as it moves from layer 1 to layer 2, and to you, depends entirely on the type of second layer used. Let’s look at the different solutions, namely rollupsTHE validiums and the L2 “disconnected” of Ethereum.
First of all, let’s explain the differences between these concepts:
- A rollup executes transactions and stores transaction data on the main chainguaranteeing strong security;
- A validium also executes transactions in a verifiable manner, but outsource data storagereducing costs, but also security;
- A L2 disconnected works independent of the main chainproviding maximum scalability, but with the lowest security, depending on its own consensus mechanisms.
The different guarantees
If it’s a rollup, the guarantee is strong: you will always have the possibility of recovering your asset on layer 1 thanks to evidence of fraud or to ZK-SNARKs which validate transactions and store data on L1.
For a validium, this guarantee may be reduced, because it depends on the reliability of data storage and consensus mechanisms specific to these systems.
Finally, disconnected systems require trust a small group of people so as not to steal funds or lose keys. Indeed, these solutions require bridges which are most of the time operated centrally.
| System type | Technology properties | Security guarantees | Costs |
|---|---|---|---|
| Rollup | Computation proven via fraud proofs or ZK-SNARKs, data stored on L1 | You can always bring the asset back to L1 | L1 data availability + SNARK-proving or redundant execution to catch errors |
| Validium | Computation comes via ZK-SNARKs (can’t use fraud proofs), data stored on a server or other separate system | Data availability failure can cause assets to be lost, but not stolen | SNARK-proving |
| Disconnected | A separate chain (or server) | Trust one or a small group of people not to steal your funds or lose the keys | Very cheap |
Unfortunately, it seems that security is an inverse function of scalability in the case of L2. Indeed, the higher the guarantee level, the less scalable the system is in the context of Layer 2 solutions.
Thus, rollups, which provide a strong guarantee of asset withdrawal to L1, require all transaction data to be stored on L1, making them less scalable due to the limitation of data space on L1.
In contrast, validiums and disconnected systems, which store data outside of L1, can process more transactions at lower cost, but at the cost of less collateral when it comes to recovering assets on L1.
Intermediate security options
However, as Vitalik Buterin points out, this is a simplification of the real state of the world of rollups. In fact, there is a multitude of intermediate or hybrid solutionsof which :
- THE Volitionsa hybrid between rollup and validium, which allow users to choose where transaction data is stored (on-chain or off-chain);
- Systems with pre-confirmationswhich allow rapid withdrawals before complete finalization, ideal in the case of Optimistic rollups.
Note that in the future, the cost of publishing data on Ethereum should drastically decrease. Initially through the deployment of proto-danksharding during the Cancun-Deneb hard fork, which should lead to ~32 kB/sec of data available on the channel. Then secondly with the deployment of full-dankshardingultimately achieving a data availability of around 1.3 MB/sec.
This will notably allow a significant improvement in the performance of rollups, which use Ethereum as a data accessibility layer.
Integration with Ethereum: essential synchronization
The cohesion between Ethereum and the secondary layers is central to the security of L2s. Thus, the latter must accurately read the Ethereum blockchainand this, at any time.
This is particularly true in the event that Ethereum comes to revert, namely going back. Vitalik Buterin explains this situation in an example. Let’s imagine that the Ethereum blockchain “turns around”. If the L2 is not able to handle this situation, it will not be aware of on-chain state changes. Therefore, it might be possible to print money on the L2 by taking advantage of this loophole.
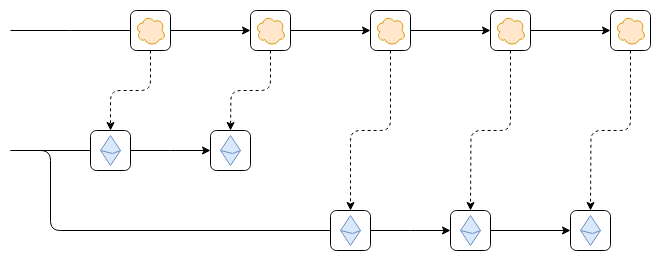

This is why Vitalik Buterin emphasizes the importance for Layer 2 systems of be able to read the Ethereum blockchain reliably and go back if necessary. He puts forward two main solutions:
- Layer 2 channels do not play that Ethereum blocks that have been finalized, thus avoiding the need to go back.
- Layer 2 chains can roll back if Ethereum revertwhich maintains functionality, but is more complex to implement.
This is a new distinction in how second-layer solutions work. Thus, each of these solutions is viable, their implementation will depend on the needs of layer 2.
Conclusion
Links to Ethereum are essential for secondary layers. Vitalik Buterin identifies two major components.
On the one hand, we have the security of withdrawals to Ethereum : is it reliable and does everyone benefit from this reliability? On the other, the ability to read the Ethereum blockchain : is it fast and how to react to exceptional events like attacks or blockchain rollbacks?
The answers vary by application, with some requiring a tight, secure connection and others being able to afford more flexibility.
While layers 2 are at the center of attention, layers 3 are starting to rear their heads. For example, Arbitrum recently deployed Orbitits program dedicated to creating L3 on top of Arbitrum.
