North Korean government hackers are hunting their future victims on the professional network LinkedIn. They pose as recruiters and trap their target with malicious documents. We went looking for these fake profiles with an expert.
Beware of beautiful promises on Linkedin, a North Korean hacker may be hiding behind the recruiter. These hackers from the People’s Republic of Korea are the regime’s privateers, constantly looking for new victims to supply Pyongyang’s coffers. In six years, they stole three billion dollars, trapping nearly a hundred companies.
In 2023, the most feared of North Korean groups, Lazarus, stole $240 million in 104 days from five victims, all in the cryptocurrency industry: CoinEx, Stake.com, Atomic, CoinsPaid and Alphapo.
The emergence of cryptocurrencies is a boon for North Korea which has found a way to finance itself while camouflaging the origin of their money. The exfiltrated sums are deposited in “mixers”, services which mix their funds with those of other users and then allow transactions to be carried out privately and anonymously.
To trap their victims, Lazarus hackers have been deploying a range of malware for several years. One method was particularly noted: hunting for employees in finance and the crypto sector on LinkedIn.
Hackers create convincing fake profiles of recruiters, executives and company bosses and then contact employees. Some cyber experts have made it their mission to detect North Korean agents before their target falls into their web.

Executive profiles on LinkedIn, Lazarus’ main target
Michael Koczwara, head of Intel_Ops_io, provides training to flush out all types of hackers. He particularly specialized in researching members of Lazarus. “ You must first find the company that will be targeted by hackers. A priori, all major companies involved in the cryptocurrency and blockchain technology sector may be affected » begins Michael. “ Lazarus will start by creating copies of the company’s sites and cloning the accounts of the company’s directors. These are the fake profiles you need to look for », he explains to us.
The latest company in Lazarus’ sights? Fenbushi Capital, a venture capital firm specializing in the field of blockchain and cryptocurrencies. This Chinese champion of investment in new technologies manages more than 1.4 billion in assets of numerous companies in the sector. A prime target for Pyongyang hackers.
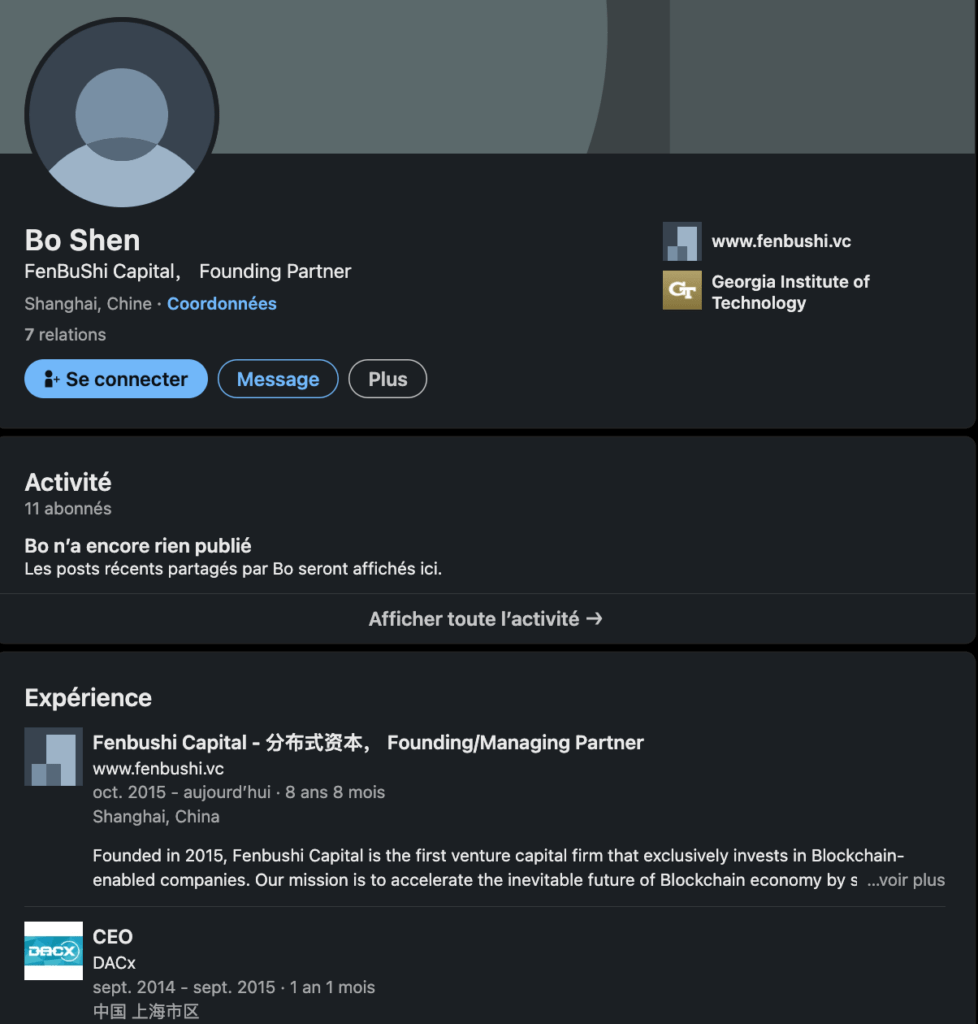
Fenbushi Capital has made the work easier since the group displays the directional circle on its site. Bo Shen, the founder of the company, was himself the victim of hacking in November 2022. Hackers stole nearly 42 million of his personal cryptocurrency assets. Hackers at the time managed to find the confidential personal question to access his wallets.
“ To find fake accounts, type the executives’ names into the LinkedIn search bar and check if there are multiple profiles under the same name » recommends Michael Koczwara. In this case, two Bo Shen, founder of Fenbushi Capital, exist on LinkedIn. If the first seems to be an old account, the second, a copy of the first, only has a few connections and subscribers.

“ We can already suspect a Lazarus profile. We must continue to look for other profiles of leaders » continues Michael. The number two at Fenbushi Capital, Remington Ong, is entitled to three profiles. The first is linked to its presentation page on the site, which already makes it more legitimate. The second was quickly spotted by cyber experts. This time, the scammers changed the target’s name, but spoofed everything else.
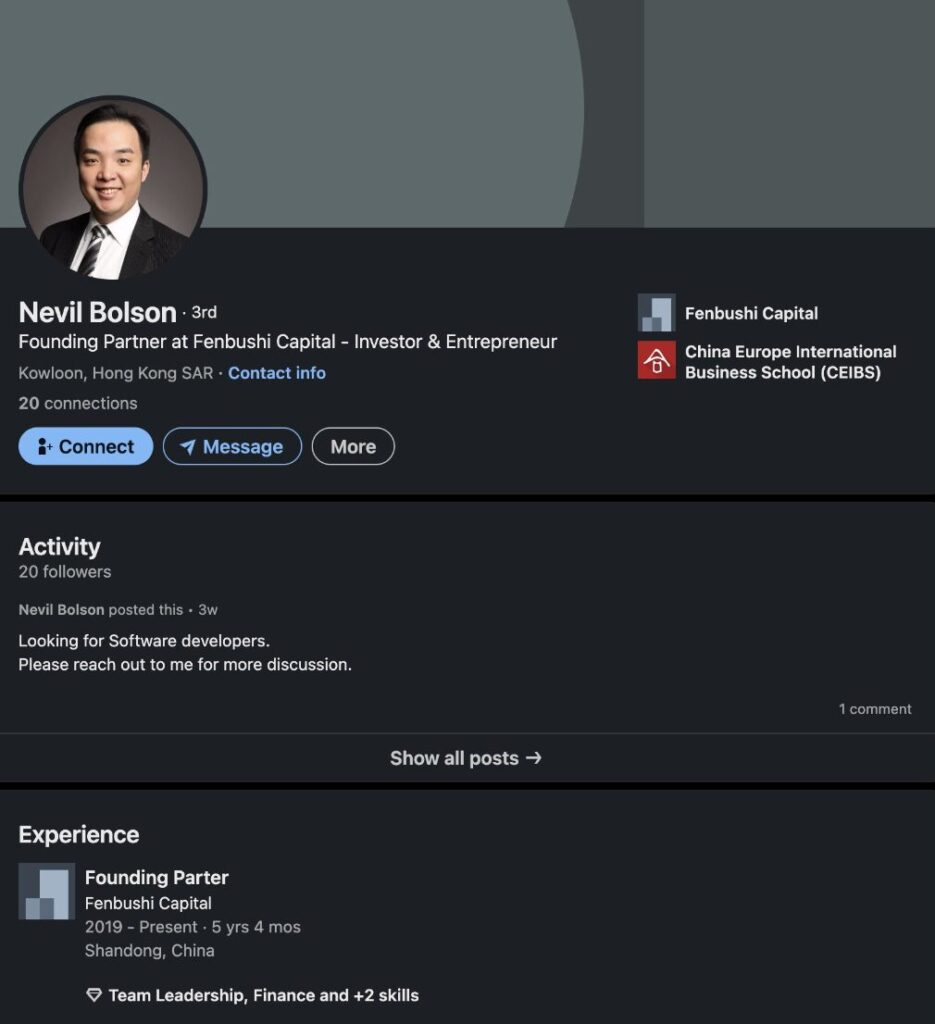

The third account is similar to Bo Shen’s: he only has one relationship and appears to be new.


“ At this point, both of the executives’ accounts have been usurped. Malicious links are another clue. Sometimes they are shared directly in the accounts and make it appear as if it is an investment conference “. The tone and direction the conversation takes with them is also essential to flush out the fake account. “They’re going to target an engineer and try to get him to absolutely download a file. Often, fake visios are offered from malicious domain names », Explains the cyber expert.
On Virus Total, a platform for identifying malicious links, two domain names created five months ago are now considered dangerous: “fenbushi[.]private-meet[.]team” and “fenbushi[.]general-[.]team”.
540 million dollars stolen using this method
Does a fake Lazarus LinkedIn profile only have a handful of followers? No, the accounts can still be much more convincing. Michael tells us “ that they sometimes buy profiles that have existed for years. The hackers then change the entire journey and identity, but keep the number of subscribers and relationships high. These accounts are even more difficult to detect “.
This method paid off at Lazarus; since in March 2022, an engineer of the Axie Infinity game, based on NFTs and crypto payments, was hacked after downloading a PDF during a conversation on LinkedIn. The employee was interested in a job offer offered to him by a recruiter on the network. However, the document sent by the usurper contained a backdoor to infiltrate the company’s network.
Result: $540 million in cryptocurrency was exfiltrated by hackers. This is to date the largest heist in the world of crypto and even cyber. And it all started from an employee who simply wanted to change companies.
Subscribe for free to Artificielles, our newsletter on AI, designed by AIs, verified by Numerama!
