It has been active since last summer in more than 100 countries: the Darcula phishing service uses the RCS protocol, and no longer SMS, to deceive its victims.
Phishing is one of the most common and effective threats to hackers. Thousands of users are fooled every month by messages and fake official sites, sometimes very convincing, with the theft of confidential and banking data.
A new type of phishing attack has been rampant since last year in no less than 100 countries, in particular because it abandons SMS to exploit the RCS protocol used by Google Messages and more recently by iMessage on the iPhone.
Darcula, phishing that uses the RCS protocol
Darcula, that’s its name, is a PhaaS (Phishing-as-a-Service), a phishing service sold turnkey to anyone who would like to set up their own little phishing business. This has obviously been used since last summer in no less than 100 countries around the world according to the site Bleeding Computerwhich cites security researcher Oshri Kalfon.
More than 20,000 domains have been spoofed in industries as diverse as postal services, airlines, banks and government. Darcula offers its “clients” no less than 200 models of fake messages and websites to deceive their victims, with almost perfect imitations of the UPS or USPS sites in the United States.
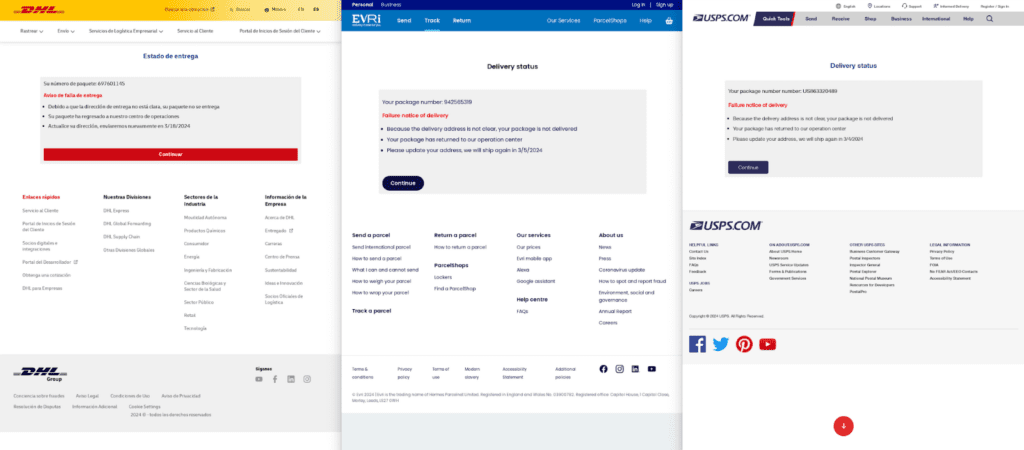
The particularity of Darcula is that it uses the RCS protocol as well as iMessage on iPhone to send its dangerous links to victims. These different protocols are sold as more secure by Google and Apple, so these messages therefore appear authentic at first glance. For the iPhone, criminals are forced to use multiple Apple IDs via macOS to send several hundred messages and thus circumvent iMessage limitations.


Additionally, because the messages are encrypted, they are undetectable by telephone carriers, “leaving spam detection on Google and Apple devices and third-party spam filtering applications as the first line of defense to prevent these messages from being sent.” ‘reach the victims’ according to the Netcraft website.
Obviously, these messages often come from dubious email addresses or numbers missing from your contact list, their dubious origin is obvious for most of them. But some attackers can use service numbers and more easily deceive their victims. This has been the case in France for several months and the recent hacking of the Ameli and France Travail services.
As always, we advise you to carefully check the origin of these messages and in particular the presence of questionable links. An administrative body will never ask you to click on a link in an SMS or RCS. And as the Netcraft site reminds us, spelling and grammatical errors are always a good means of detection.
Did you know ? Google News lets you choose your media. Don’t miss Frandroid and Numerama.
