These days, it seems unthinkable that you could send value halfway around the world without an employee or an algorithm from a centralized entity validating that you have the funds in your bank account before transferring them. How does blockchain, thanks to mathematical, computer and algorithmic processes, eliminate this need for centralization? And above all, avoid double-spending fraud.
Is it possible to copy the gold, or to reproduce it? No. Is it possible to copy a dollar bill? Yes. But you will need specific materials and the right type of paper. Then it will be impossible to give a 10 euro note to a trader, then to reuse these same 10 euros with another trader (unless you are an outstanding negotiator).
However, this is not the case with digital assets. A digital asset is a set of codes that can be copied and sent to multiple recipients. If so, digital assets in the transactional framework could be seen as a big hoax. Especially if no financial intermediary comes between two individuals to control the transactions. Fortunately, the blockchain provides the solution to this problem of double spending.
Double spending with blockchain sauce
Conceptually, this is to prevent an individual from claiming that he has more money than he actually has, and especially to spend more money than he does. In the context of a blockchain, a verification process is then necessary to allow itself to bypass the need for verification of a centralized bank. Here, the idea is that the network (the entities connected with their computers) decides with the majority of the validity or not of a transaction. The purpose is the same: the transaction will be authorized or not. However, the difference is played out at the level of the source of legitimation. It is the majority of the network which, by replacing the centralized banking institution, validates the transaction on the basis of the quantity (+ 50% of the nodes, in other words, of the computers connected on the network agree that the transaction is legitimate) rather than on the quality of the authority (a bank).
Centralized vs decentralized system
Source: economie.gouv.fr
Here we see the interest of the notion of “decentralizing” emerging. The more actors are present all over the world on the network to verify transactions, the more validators there are to legitimize the blocks that include the transactions, the more “secure” the network becomes. With nearly 15,000 validator nodes on the Bitcoin network currently, if ten or so fail, thousands more can take over without any problem (since each node has the same transaction history as all the others). Unlike a centralized entity which can be corrupted, a large decentralized system becomes difficult to corrupt.
In digital currency systems, ensuring funds are not duplicated is of paramount importance. Blockchain systems don’t work if X receives ten units and copies / pastes them ten times to create a total of 100 units. Blockchain systems also don’t work if X sends the same ten units to Y and Z simultaneously. In other words, there must be a mechanism that ensures that system funds are not duplicated.
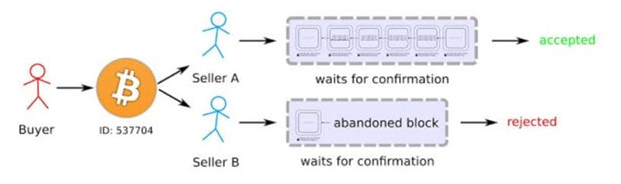
Diagram of double spending
Source: Digitemis.com
In this logic, it is necessarily necessary that each owner is identifiable and that the transactions are public so that they are verified. In other words, you have to be able to record an individual’s first transaction on the blockchain (ultimately a public register that can be viewed by everyone at any time). Example: Etienne buys 10 bitcoins for the first time in his life. Etienne will enter Bitcoin’s history as soon as he acquires his BTCs so that we can check and trace his next movements. If Etienne sends 4 bitcoins to another individual then the entire network will be able to trace the transaction. Using cryptographic protocols, the community will be able to tell if Etienne has the right to send 10, 20 or 100 bitcoins to someone else on the network (the concept of double spending). In the case of the Bitcoin blockchain, our personal information is encrypted so that it cannot be directly identified under our own name. This notion will be the subject of an entire episode.
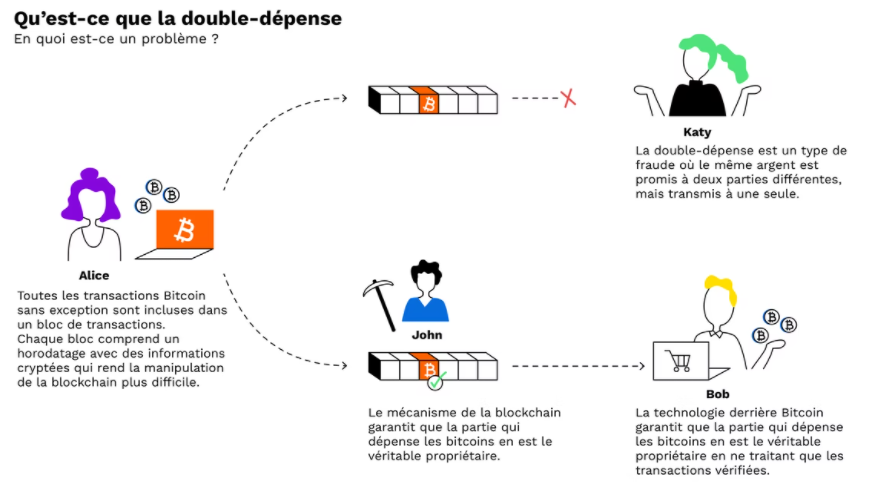
Double spending system
Source: Bitpanda
We understand that it is going to be difficult to lie as everything is visible and traceable on the public ledger of transactions. Each transaction is also irreversible. What is engraved on the blockchain is final and tamper-proof.
Bitcoin, the time limit.
Imagine that a user wants to use their bitcoin to make multiple purchases at different merchants simultaneously. On average, a block is checked and validated every 10 minutes on Bitcoin, which allows a scammer to use his bitcoin to as many traders as he wants as long as the first transaction is not validated by the network. As a reminder, a block contains around 4000 transactions for a weight of 1MB.
Our crook therefore holds 1 bitcoin. He knows that he can simultaneously use his bitcoin with several traders (the principle of double spending). Miners will take X minutes to validate the first transaction made with their bitcoin while the others will be rejected by the network. Traders will then have to wait until the transaction is verified and validated by minors to avoid a scam.
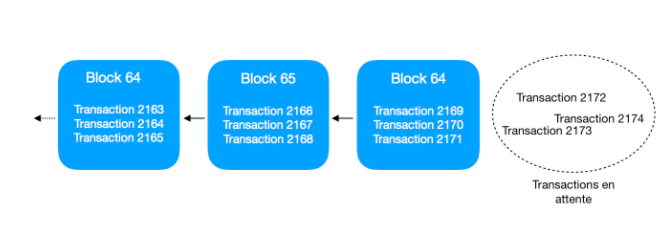
Diagram of pending transactions
Source: oulasri.github.io/
This verification requires complex mathematical calculations to verify these transactions. This is where miners (using computers connected to the network) come in to verify operations. Imagine computers that constantly perform calculations to find a mathematical solution to validate the block, in other words to close it and move on to the next block. But to verify these transactions and therefore the debauchery of energy generated, the “proof of work” mechanism provides for remunerating these minors.
Proof of work is a consensus mechanism used to confirm that network participants, called miners, calculate valid alphanumeric codes (called hashes) to verify Bitcoin transactions and add the next block to the blockchain. We will come back to “proof of work” up and down throughout the saga. Here we confine ourselves to the concept of double expenditure which is a characteristic of this “proof of work”. (Proof-of-Work for the Anglo-Saxon version).
The problem of the Byzantine generals
The Byzantine Generals Problem is a computer problem that was formalized by Leslie Lamport, Robert Shostak and Marshall Pease in 1982. It is a metaphor involving generals besieging an enemy city. A problem brought up to date by the mysterious Satoshi Nakamoto to illustrate the solution provided by Bitcoin.
The problem of the Byzantine generals can be understood by imagining a city that must be conquered. It cannot be conquered by just attacking from one side as it has adequate defense to fight on one side only. However, if two armies attacked from both sides, the city would be easily defeated. Knowing this, the generals decided to divide their army in half so that the armies could attack the city from both sides at once. The key, however, is for both army groups to attack the city simultaneously. If there was no digital communication between the two generals, it would be very difficult to ensure that both armies attack the city at the same time. Even if the generals used a messenger to coordinate attacks, the generals might not be able to trust the messenger. If city security were to capture the original messenger and send a fake one to the other side, for example, the attack will fail. Is there a way to authenticate a message without trusting the messenger (trusted third party)?
From generals to Satoshi
The solution to the problem of the Byzantine generals is not easy. Perhaps some sort of encryption would help the generals share a passphrase that decodes and verifies the authenticity of the underlying message. In a computerized world, decoding simple algorithms is very easy. For this reason, the hashing algorithms (mathematical function) proposed by Satoshi Nakamoto have been extremely helpful in increasing the complexity of these algorithms.
Specifically, Satoshi Nakamoto proposed a data structure known as a blockchain where participants (nodes) execute complex algorithms to solve various mathematical problems. Once a mathematical problem has been solved, a block is created and communicated to the entire network.
Likewise, transactions initiated by users are also verified by these nodes. This is because a transaction is not immediately added to the blockchain. It is only added to the blockchain after a node has created a block using computing power. In return, the node is rewarded with digital currency. And yes you will understand, the mathematical calculations of transaction verification require a large amount of energy (electricity), we had to imagine a way to reward these nodes to encourage them to validate the transactions. The bitcoin reward was then brought. We will come back to this later as well, as this topic requires a dedicated article.
Additionally, transactions are communicated over the live network, which means every computer on the network knows about every transaction as it occurs. If an intruder tries to communicate a fake transaction or spend the same coins twice on the network, it will be rejected because other nodes will invalidate it. The blockchain via proof of work is therefore a practical way to get around the problem of double spending and the problem of Byzantine generals.
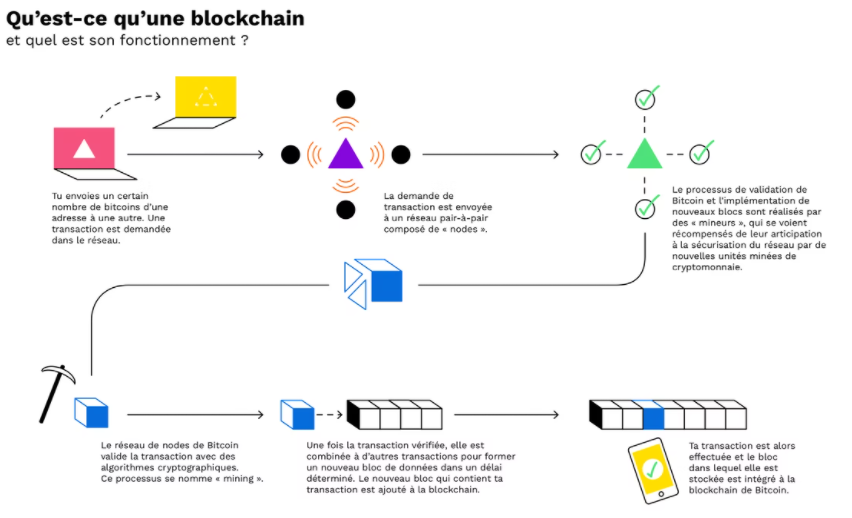
Diagram of a blockchain
Source: Bitpanda
It is clear that Bitcoin has proven to be inviolable since its creation more than thirteen years ago. The “proof of work” mechanism proves, for the moment, the possibility of dispensing with a trusted third party to carry out a transaction on the blockchain. In the next episodes we will explore how we are identified on the network (public key and private key) and the different existing blockchains (permitted, private, public). See you for the rest of the saga in the columns of Zonebourse very soon.
