Researchers have published a new technique to simulate iPhone shutdown for monitoring.
Dubbed “NoReboot,” ZecOps proof of concept is described as a method that can bypass the normal practice of restarting a device to clear malicious activity from memory and gain persistence on the device.
Presenting a GitHub analysis and public repository this week, ZecOps explained that the NoReboot Trojan simulates a real device shutdown while providing cover for the functioning of the malware, which could include covert hijacking of the mic’s capabilities and camera to spy on the phone owner.
“The user cannot sense the difference between a real stop and a ‘false stop’,” the researchers say. “There is no user interface or button feedback until the user turns the phone back on. “
The technique causes the expected shutdown event by injecting code into three daemons: InCallService, SpringBoard, and backboardd.
When an iPhone is turned off, physical indicators indicate that the operation was successful: a ringtone or sound, a vibration and the appearance of the Apple logo on the screen. But by disabling “physical feedback” the malware can create the appearance of a shutdown while a live connection to an operator is maintained.
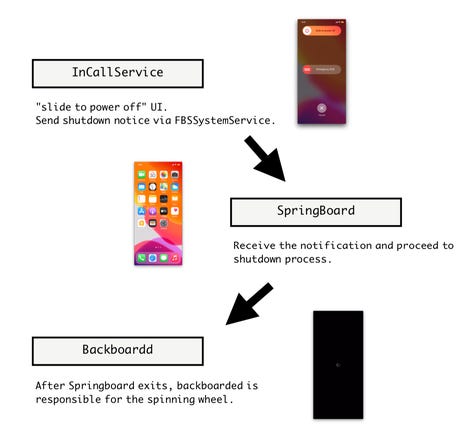
Image: ZecOps.
“When you turn off the device, it’s actually a system app /Applications/InCallService.app that sends a shutdown signal to SpringBoard, which is a daemon responsible for the majority of the interaction with the user interface, ”the researchers explain. “We managed to divert the signal using the Objective-C method -[FBSSystemService shutdownWithOptions:]. Now instead of sending SpringBoard a stop signal, it will notify both SpringBoard and backboardd to trigger the code we injected into it. “
The display indicating a shutdown process can then be hijacked via backboardd and the SpringBoard function can both be forced to quit and blocked not to restart. ZecOps says that by taking control of SpringBoard, a target iPhone can “look like” it’s not turned on, which is the “perfect disguise.”
However, users still have the option to force restart. This is where the alteration of the backboardd comes in: by monitoring user inputs, including the length of time the buttons are held, a restart can be simulated just before a real restart takes place, for example by displaying the Apple logo earlier.
“Preventing users from manually restarting an infected device into believing it was successful in doing so is a notable malware persistence technique,” comments Malwarebytes.
As the technique focuses on deceiving users rather than vulnerabilities or bugs in the iOS platform, this behavior will not be fixed with a simple patch. ZecOps indicates that the NoReboot method has an impact on all versions iOS and that only hardware indicators could help detect this form of attack technique.
A demonstration video is available below:
Source: ZDNet.com
